While finding the private key is a bad thing itself, you can try stepping a step forward – find out the password of the private key and log in with it. This is a thing you might need to do in a CTF, or by hacking a vulnerable machine. Let’s see how to crack SSH private key with John the Ripper and ssh2john, one of the John modules. But let’s start from the beginning.
For someone who is new in the ethical hacking world, there is one tool you should get familiar with.
Its name is John the Ripper.

It is a tool that is widely used for cracking passwords. Even though originally it was built for Unix-based operating systems, nowadays it can be run on fifteen different platforms. Released in 1996 gradually it became a widely adopted tool that is still relevant nowadays.
This is a tool that you will definitely use during your career as an ethical hacker or bug bounty hunter. If you are into solving CTFs and hacking vulnerable apps, John is a tool you will have to use frequently.
John the Ripper comes with detection of different password hash types, such as Kerberos, LM hashes, MD4-based hashes of LDAP or MySQL services.
John has plenty of modules that can be used for performing dictionary or brute force attacks for different targets. One of the modules that will be covered in this post is called ssh2john.
How to Crack SSH Private Key With John the Ripper
It all starts by obtaining an SSH private key of a user. If you have the private key of the compromised machines’ user locally, half of the job is done. Well, almost. If the password of the SSH private key is complex enough, it might potentially take ages to brute force it. But if you are doing this for solving a CTF, usually the passwords are not complexity monsters.
Before brute-forcing the passphrase with John the Ripper, we should convert the contents of a private key file. And for converting it into the needed “john format”, to the help comes ssh2john. This module arrives with the default John installation. It creates a hash that we will use just in the next steps.
For the purpose of this tutorial. let’s say we created a new private key with a simple passphrase.
ssh-keygenKeep in mind that OpenSSH is used by the ssh-keygen of the Kali Linux, so this example won’t be accurate with the private key generated on Kali. But with the private keys of other distros, there are no problems.
The word “monkey” was used for a passphrase.

The next step would be to run the ssh2john script, and write the results of it into a file:
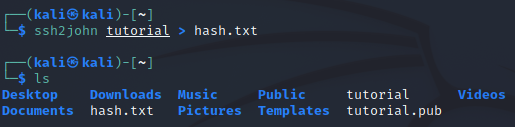
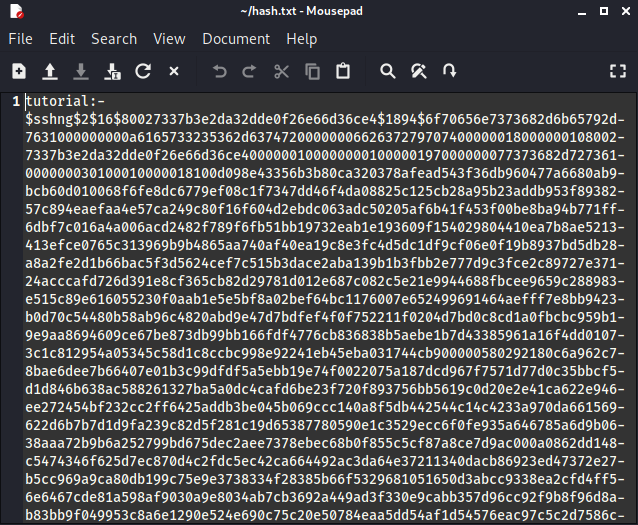
A new file should be created. The content of the file doesn’t look very user-friendly, but don’t worry, this file is for John.
Now we can use John for cracking SSH private key. We will use the rockyou.txt dictionary for this task:
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txtAs the password was one of the first rockyou.txt words, BINGO! By using the John we got the SSH private key’s password.

NOTE: if you are using fresh Kali Linux installation, you might need to extract the archive with rockyou dictionary in order to use it. You will find it in the /usr/share/wordlists.
Ssh2john: Command Not Found
It might be devastating to spend time fixing a tool instead of doing actual penetration testing. But once in a while, it happens – tools do not work as expected.
Some of the John The Ripper modules, you can start by simply specifying the name in a terminal. For example, zip2john would start with a simple command:
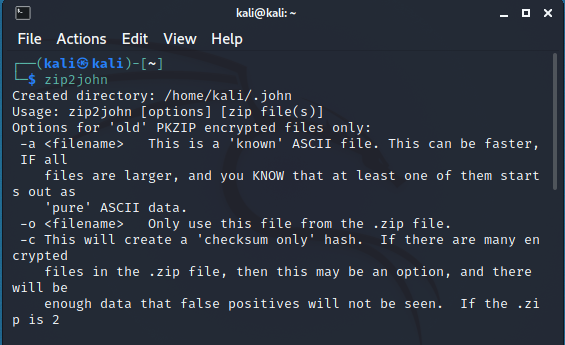
But with the ssh2john it is a different story. By starting ssh2john from the current directory, you will get a Ssh2john: Command Not Found error.

This is where you can find Ssh2john on Kali Linux:
/usr/share/john/ssh2john.pyIf you are using TryHackMe attacker box, this is where you can find Ssh2john on TryHackMe VM:
/opt/john/ssh2john.pyWe will continue this tutorial with the Ssh2john location on the Kali Linux.
Moving on, change directory to /usr/share/john, and run the file as a usual Python file:
python ssh2john.pyThe script should start. Now all you need to do is to “feed” a private key to it. The whole procedure was shown in the previous subsection of this article.
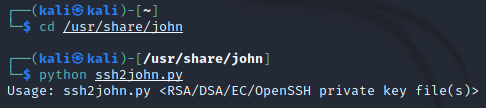
NOTE: this is a module written with an old Python 2, so running it as a Python 3 script won’t work.
If you are planning to crack SSH private key with ssh2john in the future, you might want to create an alias. Open the .bash_aliases file (or create it):
sudo nano ~/.bash_aliasesAnd add the following alias to the file:
alias ssh2john="python /usr/share/john/ssh2john.py"Save the file:

Now reload the file:
source ~/.bash_aliasesNext time you will need the ssh2john, you can simply run it by its name:
Conclusion
Should you try cracking SSH private key when doing a penetration test?
It depends on the engagement rules. But once again, gaining access to a private SSH key is a critical security issue in itself. Reporting this finding to the client is enough. But if you do have the time for going deeper, you might want to use ssh2john for cracking the SSH key. Maybe you will log in to the system with this private key and will find there other vulnerabilities. Who knows.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.


i run into similiar question while doing pen-100, but ssh2john said no passwords,