Encrypting your computer disk is crucial. There is nothing worse than losing your personal data. Not only the data can be used to extort you, but you might immediately experience financial losses. That’s why should know how to encrypt Kali Linux after the installation?
As the Kali Linux is usually used for working with confidential data, it is very important to take care of the security of data stored on your machine. If the findings of the client’s target you are working with will be leaked, the vulnerabilities might be exploited. Which all would result in a serious trouble to your client, and to you.
Encrypting Kali Linux Disk BEFORE Installation
As the Kali Linux is not encrypted by default, you should select the encryption manually.
Encrypting the disk during Kali Linux installation is pretty simple and straightforward. There is a separate option on the Partition Disks page. After selecting this option you will be able to select the disk and set a password.
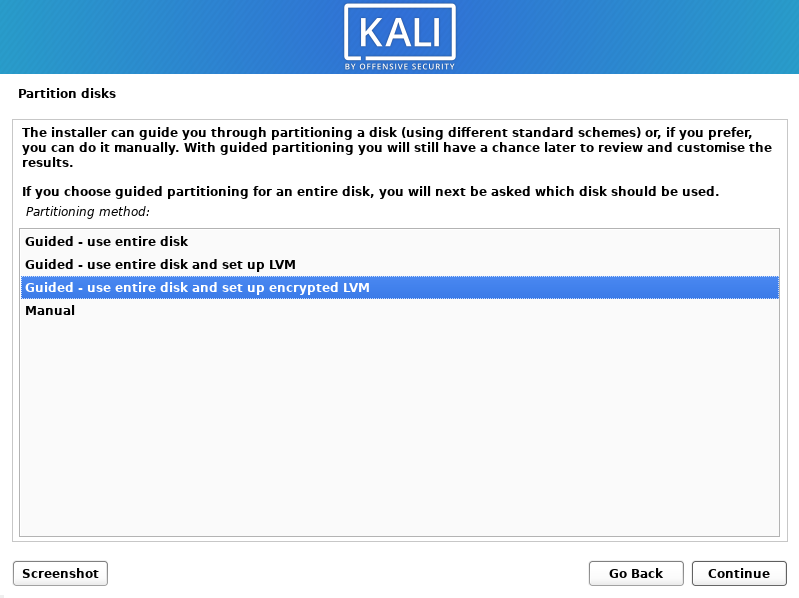
This is a really simple process. By following this your disk will be encrypted with LVM and LUKS.
However, it is possible that you choose the other option that does not include encryption. Rookie mistake. If you are installing it for the first time, there is a chance that you have missed it.
How to Encrypt Disk of Kali Linux AFTER the Installation
First step of encrypting the disk, is to install the ecryptfs-utils package.
sudo apt-get install ecryptfs-utils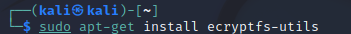
After this, you should boot in recovery mode and execute the following command:
ecryptfs-migrate-home -u user_to_migrateAfter the migration, logout and login as your user:
exitFor setting the passphrase, use the following command:
ecryptfs-unwrap-passphraseAfter everything is done, reboot. You might then delete the temporary files created by the ecrypt.
Note: this will only encrypt the home directory of your user. But it will not perform full disk encryption. If you want to fully encrypt your Kali Linux disk, it is really easy to do this during the setup.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

