SHA-1 (secure hash algorithm) is a cryptographic hash function. At the time it was created, it was considered being secure, but nowadays it isn’t secure no more. The hash function, that was created in 1995 by US NSA (National Security Agency), is considered being vulnerable since 2005.
NIST (National Institute of Standards and Technology) had deprecated the SHA-1 algorithm in 2011.
And while it is still more secure than the older algorithms, such as MD5, using the SHA-1 for hashing passwords, is a risk. The SHA-1 algorithm is obsolete.
It takes 110 years to crack a SHA-1 password with a single GPU. But if you have the resources, and know what you are doing it will take you less than a year. Unsalted SHA-1 hashes are an easy prey for the attackers, especially when there are rainbow tables to perform such attacks.
Table of Contents
How Does this Hashing Algorithm Work?
We will try to explain how does the SHA-1 works in a simple words. If you are interested in the technical implementation of the hash algorithm, you can refer to the official papers.
This is the simplified explanation of the SHA-1 algorithm from the technical perspective:
- First of all, variables are initialized. These variables are defined in the SHA-1 specification and they have predefined values
- Then the message (value that the hash should be generated for) is being preprocessed by adding the needed bits
- After that, the message is processed in 512-bit chunks. Function and constants defined in the algorithm are used. Iteratively, 80 functions are used
- As a result, a SHA-1 hash value is generated
This is just a general overview of the algorithm. In practice, there are more things under the hood.
As it was stated at the introduction, this algorithm is not secure. The reason why SHA-1 considered insecure, is that the generated hashes aren’t unique. Because of the collision attacks (that will be covered in the next sections of the article), two different hash values can produce the same hash value.
How Secure is the SHA-1?
The truth is, it is not secure.
The reason why SHA-1 considered insecure, is that the generated hashes aren’t unique. Because of the collision attacks, two different hash values can produce the same hash value.
Let’s see how it might affect users in the real life. Hypothetical situation – system developer had made a deadly sin and implemented SHA-1 for saving passwords.
So, we have a user that uses a password “polarbear”. SHA-1 algorithm used for the password produces a specific hash value.
Then, let’s say, another user uses a password “fennecfox”. After using the SHA-1 hash algorithm, a hash value is generated, which is equal to the hash value of password “polarbear”.
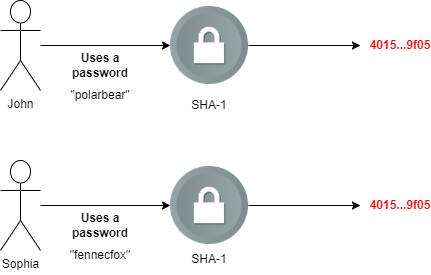
This is just a dumb example, both of the passwords used in this example does produce different SHA-1 hashes. And the collision attack is more likely to occur for the document files.
This weakness of the SHA-1 algorithm was known since the 2005. But this has not been validated practically, as it requires a lot of resources to do so.
Until 2017, when the Google successfully performed SHA-1 collision attack.
Google proved that it is possible to crack SHA-1 for less than $100,000 spent on cloud computing power. They have managed to do this in one year with 110 GPUs. Of course, they also had their own method to do this.
Below there is an infographic that shows results of an experiment.
When and Where Are Hashing Algorithms, Such as Sha-1 Used
There are two big use cases for the SHA-1, or any other hashing algorithm:
- Using it to store passwords – although it is not the safest algorithm, and there are much better alternatives
- Checking integrity of the files – if you want to make sure that the document was not altered since it was sent to you, you can generate hash value of the received file and compare it to the original hash value. GIT also relies on SHA-1 hashes to check the integrity of committed files
But are there any SHA-1 alternatives? There sure is.
Some of the secure SHA-1 hash algorithm alternatives are:
- SHA-2 – created as a successor to SHA-1. This algorithm is recommended by NIST. The algorithm is more secure, but it takes about 20 to 30 percent longer to calculate the hash value.
- SHA-3 – algorithm was released by the NIST in 2015. It was created during a competition. It works differently than the earlier SHA algorithms.
- Argon2 – another algorithm that had born during the competition in 2015. Argon2id is recommended by the OWASP to hash passwords.
- Blake – an algorithm that is also considered as being secure by NIST.
Can FBI Crack the SHA-1?
FBI is likely to be able to crack the SHA-1 hashes. With the resources and knowledge the FBI has, they can do a lot of things. For example, they can crack passwords of most of the mobile phones. And the newest mobile devices are definitely using stronger algorithms than SHA-1.
But don’t get confused – hashing and encryption algorithms are not the same. What does this fact illustrate, is that if the government agencies have the expertise and resources to crack encryption algorithms, the same is probably true about the hashing algorithms.
If Google had managed to crack it in 2017, who knows for how long various intelligence agencies across the world were able to do this. After all, SHA-1 algorithm is insecure for over 15 years
Final Words
For a long time SHA-1 is known to have weaknesses. It is not safe to use it for storing passwords, communication with a website (by using it as a part of the cipher suites), or for verifying integrity of the files. Collision attack can be performed for a relatively low amount (for the criminals, but not for the security researchers). So, the SHA-1 is obsolete.
It is recommended to choose more secure hashing algorithms, such as: Argon, Blake, SHA-3, SHA-512, or any other algorithm that is considered being secure enough.
If you are hashing the passwords, make sure you use the salt. In this way, an attacker will not be able to perform rainbow table attack.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

