One of the most important skills you’ll need to succeed in ethical hacking is the ability to use a variety of tools to begin your penetration testing procedure. Even while browsers aren’t the the type of tools that will help you to find vulnerabilities, it can help you accomplish a wide range of goals – from scanning a whole website to hijacking secured test sessions. For this reason today we are going to review the best browsers for hackers.
Because you, as an ethical hacker, are working with different systems, you must use a safe browser. Browser that is hacked not only puts you at risk, it might also put the client you are working with, at risk. There is a wide range of these browsers on the market. Users can download ethical hacking browsers with ease. Most Ethical Hackers and Security Researchers prefer to use browser while executing web application penetration testing. A large part of its appeal is the abundance of additional tools it offers, such as the Web Developer Tools, various additional Extensions.
Ethical hackers and security researchers may use a variety of browsers to automate or speed up their testing. The privacy and security features built into today’s online browsers are becoming more and more complex. In addition to applying any new updates, make sure you verify your browser’s security settings. As an example, you may prevent websites from monitoring your movements by using a browser that does not allow cookies to be installed.
We’ll take a look at a few browser that can make life a little easier for ethical hackers down the road.
Without further ado, here is the best browsers for hackers.
Table of Contents
Tor Browser

The famous browser that is used for accessing the darknet. Free and open-source Tor Browser software provides anonymity online and increases your security and privacy while surfing the web. The TCP protocol is used by Tor to provide anonymity for publishing, online browsing, instant messaging, and other tasks. When you’re done surfing, the advanced browser immediately deletes all cookies to prevent third-party trackers and advertisements from tracking your activities.
If you are trying to stay anonymous online, this is a browser to go. Although it has some disadvantages that we will talk about later.
How does the Tor Browser works?
The vast majority of the world’s open connections are used to carry all online traffic. More than 7,000 relays make up Tor’s massive volunteer overlay-network, which serves as a conduit for traffic. By the time your data or traffic reaches its final destination, it will be practically difficult to trace its original source due to the additional encryption that is applied with each data relay.
What are the advantages of the browser?
- Each page you visit is isolated. In this way no third-party trackers and advertisements will be able to follow you around. When you’re done surfing, any cookies you’ve set will be deleted.
- Everything you doing inside the tunnel won’t be seen to anyone. The traffic is encrypted and all the man-in-the-middle will be able to see, is that you are utilizing the Tor anonymity network.
- As by using the Tor you get another IP, you might be able to access websites that aren’t visible from your IP as your ISP had prohibited them.
Can Tor browser be used for penetration testing?
It sure can be. However, it has it is pretty slow. If you are using it for performing actual penetration testing, it will just take so much time
Mozilla Firefox

Firefox has been there for a while. Almost every ethical hacker and security researcher prefers the Mozilla Firefox browser for web-based application penetration testing. If you are using the Kali Linux, you must have noticed that it has the Firefox installed by default.
When compared to other browsers like Chrome, Safari, and Opera, Mozilla Firefox has shown to be more feature-rich. A large part of its appeal is the abundance of additional tools it offers, such as the Web Developer Tools, Extension for developers, Task Manager, and many more useful ones. Ethical Hackers and Security Researchers may utilize a variety of extensions to automate or make their testing more efficient.
Brave Browser

Brave is a web browser that has an integrated ad blocker. But not only that, it also disables malicious cookies, which makes your browsing more secure. There are a plethora of alternatives available for individuals who desire to block trackers, however the Brave browser makes it simple and this function is built into the browser itself.
The majority of advertising networks use tactics to attempt to identify and monitor you while you navigate the internet. Brave browser prevents all of this from happening, enabling you to surf freely. Additionally, in addition to the privacy benefits, there is a performance gain.
There are also performance gains, as Brave blocks unnecessary JavaScript code that is used to display ads or track your behavior.
The Brave also has this cool dashboard that shows how many bandwidth and time it had saved for you. If you are a heavy user, the number of trackers and ads blocked might blow your mind.
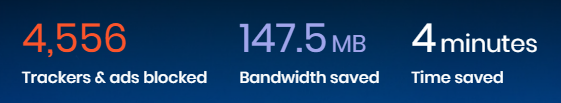
All the mentioned features makes the Brave browser one of the browsers for ethical hackers.
LibreWolf

Privacy, security, and freedom are the core values of Librewolf. The browser is a fork of the Firefox that focuses on these aspects. It is also an open source project, so everything is visible and anyone can join to the development.
Browser has private search based on privacy-conscious search engines, such as DuckDuckGo, Searx, or Qwant. It also utilizes content blocker.
Tracking and fingerprinting tactics may be thwarted using LibreWolf, Additionally, LibreWolf intends to disable anti-freedom elements like digital rights management (DRM). Firefox’s distracting features are no longer an issue with LibreWolf, which provides a private browsing experience without the need for user intervention.
Epic

Epic is a browser based on a Chromium, an open-source version of Google Chrome. The best thing with the Epic, is that it had removed all Google tracking scripts and does not allow anyone to track you. You can be sure that you are always browsing in “private mode”. Epic does not save your browsing history other than the ability to move between open tabs, therefore closing a tab does not leave a trace on your computer that you visited a certain website
As the browser is private by design, no date is collected. And this makes it one of the best browsers for hackers.
DuckDuckGo

You are probably familiar with the DuckDuckGo – search engine with the duck logo. The search engine is famous for being anonymous. It provides private search, blocks various third party trackers, and encrypts data. DuckDuckDuck go also has a browser that we are going to review in this article
As with its mobile browser software, DuckDuckGo’s new desktop browser app will enable users to do internet searches without being tracked or having cookies installed on the devices. The browser is more secure, private, and speedier than Chrome in terms of browsing. The mobile version of DuckDuckGo’s browser may already be downloaded from the company’s website. DuckDuckGo began supporting Apple Maps in 2019 and has since made several enhancements to the app’s functionality on Apple devices. DuckDuckGo for desktop uses the same rendering engines as the DuckDuckGo mobile applications; it does not employ a Chromium derivative like other browser solutions.
With a Windows version coming soon, desktop browsers are now in closed beta for Macs. DuckDuckGo is presently looking for beta testers but has not yet announced a release date. There will be no “misleading” warnings or “levels of privacy protection” on the DuckDuckGo browser, the business said in a blog post. As DuckDuckGo put it, “There is never a bad moment to block firms from eavesdropping on your search and browsing history,” and that is why it calls itself a “privacy browser,” not a “privacy browser.”
Pale Moon

When it comes to browsers, Pale Moon has quite the resume. Pale Moon isn’t simply another “outdated and unsafe Firefox clone,” as some have claimed. This claim regarding Pale Moon is most likely false, at least according to the vast majority of reliable sources. Pale Moon is a fork of Firefox that has grown into its own product with due cause. Pale Moon lays a lot of emphasis on being a fast, safe, and private browser, despite the fact that its primary focus seems to be on customizability. The fact that the code of Pale Moon is open source, makes it one of the best browsers for hackers.
However, one security incident related to the Pale Moon browser is worth mentioning. On 10 July 2019, it was discovered that malware had been injected into the executables of the Pale Moon browser’s archive server. On the next day, this vulnerability was identified. The exact date of the initial breach is uncertain.
Chromium

Chromium is an open-source version of the Chrome. While it does provide more visibility than then Chrome, it is still a product of Google. While this might not be the best private browser on the market, it is still worth your attention.
For the most part it’s the same as Google Chrome, except it does not require you to unintentionally hand up any of your personal data to the search engine. For Google’s Chrome browser, the open-source Chromium project aims to release the original source code. As a result, Google is able to accept feedback from outside sources and iterate swiftly on new ideas. Every once in a while, new versions of the Chromium browser are being released, so it has a big support.
Is Google Chrome Spying on Me?
One of the biggest concerns of using the most popular tech products is that the big companies are spying on its users. You can occasionally see accusations in the media for Google acting like an evil corp. Let’s see of there are really privacy concerns while using Google Chrome.
Using Google Analytics, you can keep tabs on the visitors to your site. It may be used in conjunction with Google’s advertising platform. In this way, the website administrator may gather a plethora of data about the individuals who visit the site, including as their computer’s display resolution, operating system, mouse movements, and the links they click. Their ability to tailor content and design for specific consumer needs is greatly enhanced as a result of this. In addition to the fact that it’s free and incredibly sturdy, Google Analytics is also hosted by Google, making it exceptionally quick to load. Many websites/servers have something like this at the fundamental level,
Yes, Google Chrome monitors your browsing history. In fact, almost all web browsers do the same. As a result of their responsibility to keep you logged in and provide you with accurate information regarding website security, they must. For obvious reasons, Google keeps tabs on you even when you’re not hooked in to their service via your browser. Extensions you’ve installed may gather information about your browsing habits, such as how quickly your website loads or which adverts are being shown to you. Syncing your history and passwords to Google’s servers in encrypted form is possible if you are signed in to Chrome itself, such as an account.
Install Chromium if you’re worried about Google monitoring your activities. With Chrome’s open source core, Google can develop its own services on top of it. There are no major drawbacks, and it has a lot of the same features.
Conclusion
There are many great privacy based browsers for hackers. Make sure you choose the right one if you want to protect your privacy If you do not need any specific functionality, look for a browser that disables unnecessary JavaScript and blocks any external trackers.
Technology enthusiast and blogger in my free time

