Moodle is one of the most popular learning management systems (LMS) that provides environment for learning, testing, and training. This software is used by a big number of organizations across the globe. As this software provides a platform for educational organizations, it is mainly used by schools and universities. However, because of the COVID-19 pandemic, it gained a huge popularity between other types of organizations. And as this is such a common software to have for SMB (small-medium business), today we will talk about the Moodle penetration testing.
Table of Contents
Why Do Companies Use Moodle?
Before diving into the Moodle penetration testing, we have to fully understand why this software is used for, in the first place:
- To periodically raise employees security awareness. As the cyberattacks are increasing each year, it is very important to make sure the employees know how to recognize threats. And of course, raising security awareness is required by GDPR, and other laws. Moodle is a perfect fit for providing learning material, and then testing gained knowledge.
- To test employees. This can be used for usual business activities. For example, you can provide fire safety test that each employee has to pass regularly.
So, from the perspective of an enterprise, there are many use cases how the Moodle can be useful. And that’s the reason why the product is so popular and is utilized by almost every company. If you are wondering why this specific product is so popular, there at least few solid reasons:
- Software is pretty multi functional and can customized according to your needs
- It is open-source – it means it is free
- Moodle has been there for many years, so it earned its name
According to the Moodle statistics, there are over 180 000 Moodle sites:

Moodle From the Security Perspective
Before diving into the analysis how the Moodle can be exploited, it is important to understand technologies that the software is built with.
Moodle is a software programmed with PHP. It is open-source and distributed under the GNU General Public License.
First version of Moodle was released in 2002.
During the years the product received many releases and it evolved into a powerful and solid learning system. One of the key features of the Moodle, is that it uses plugins. Just like with the WordPress, you can add needed functionality by installing plugins.
Number of databases are supported by the Moodle, including the MySQL. And when it comes to the web servers, the most popular ones, such as Apache, can be used.
Even though Moodle is a pretty powerful platform having many features, we won’t discuss it here. For us, as a security researchers, different aspects are more interesting. Let’s use an example of a Moodle that is installed on a medium size company. In this situation, a few assumptions can be made:
- Moodle might contain personal data – it can be either entered directly when creating an account for the employee, or might be synchronized from another system.
- It might have accounts created manually in the Moodle, or might use the SSO, when the external entity authenticates users. However, Moodle has 17 different authentication methods, so the previously mentioned methods are just a few from more than dozen.
- If the Moodle is exposed publicly, it might become an initial attack vector – so the security of the software should be taken seriously. We will cover in this article how we can perform vulnerability assessment on Moodle.
As you can see, the fact, that the Moodle might contain personal data, it is likely to become a target of criminals.
And if you are a bug bounty hunter, you can be sure that the Moodle is something organizations are more concerned of than some of the other business applications. If you found that Moodle is in scope of the bug bounty program, this should definitely be one of your targets.
Moodle Penetration Testing Checklist
A few activities that will help you while conducting a Moodle vulnerability assessment:
- Check for Moodle exploits on Metasploit database
- Perform DAST type vulnerability scanning
- Use SAST type vulnerability scanning (if you have the source code)
- Perform scanning with Moodle scanner
Performing Penetration Testing on Moodle
When it comes to the Moodle penetration testing, there are many effective tools. Some of them, such as Metasploit, are generic, yet still useful, and some of the tools are specialized and are developed for Moodle pentesting.
In over 18 years, there were 432 vulnerabilities found in the various versions of the Moodle.
Note: there are two issues that even though it might look like vulnerabilities, they are not. One of them is Sesskey that is used as a parameter. In Moodle this is how the CSRF token is called, so this is not the real session ID. Another issue is with the XSS. Moodle has admin functionality that is able to inject HTML into the parts of the website (such as footer or header). Naturally, administrator is able to inject scripts, so this is a feature and not a vulnerability
Now let’s see what tools we might use to find them.
Metasploit
One of the best tools when it comes to exploiting a system, is the Metasploit. This is a penetration testing framework developed by Rapid7 that is de facto standard when it comes to the pentesting frameworks.
To find an exploit applicable to Moodle, we might use the Searchsploit. This tool queries exploits databases and identifies if there are any ready exploits for a given system. We can simple utilize it by executing the following command in terminal:
searchsploit moodleAs a result we will get all relevant exploits:
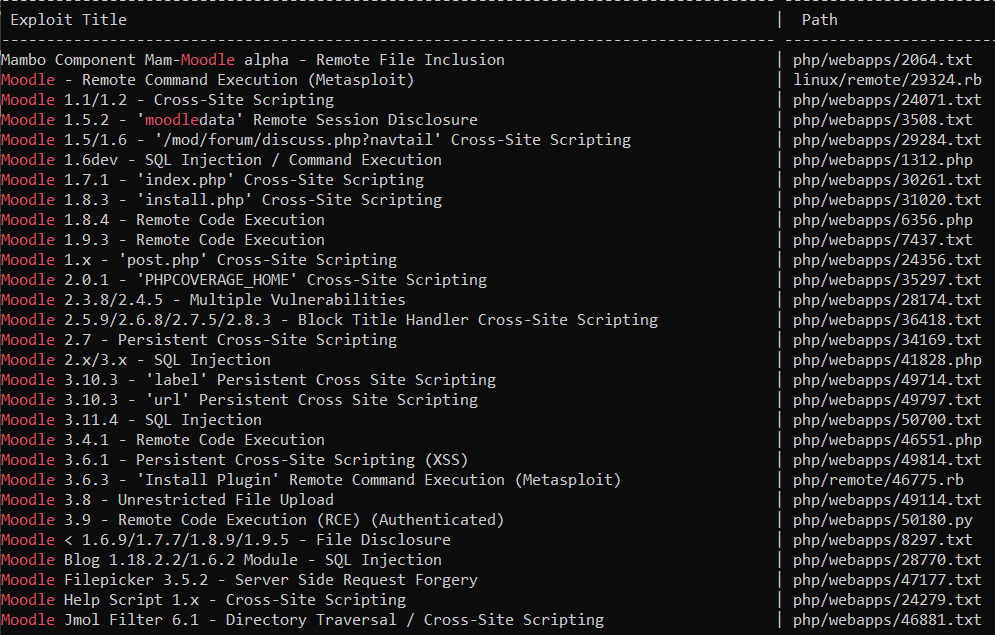
Now we can analyze if one of them can be used to hack Moodle. If so, we could use Metasploit to run the exploit.
Moodlescan
A great way to understand if the Moodle is vulnerable, is to use a specialized scanner. And one of them is Moodlescan. First of all, you must clone the tool from GitHub repository:
git clone https://github.com/inc0d3/moodlescan.gitThere is how to use Moodlescan:
python moodlescan.py -u https://example.com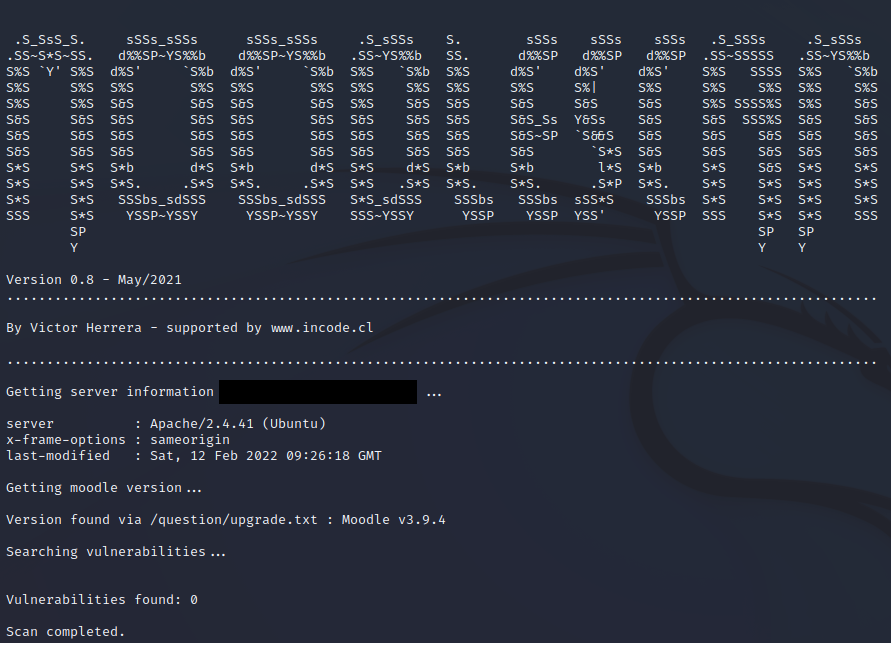
OWASP ZAP
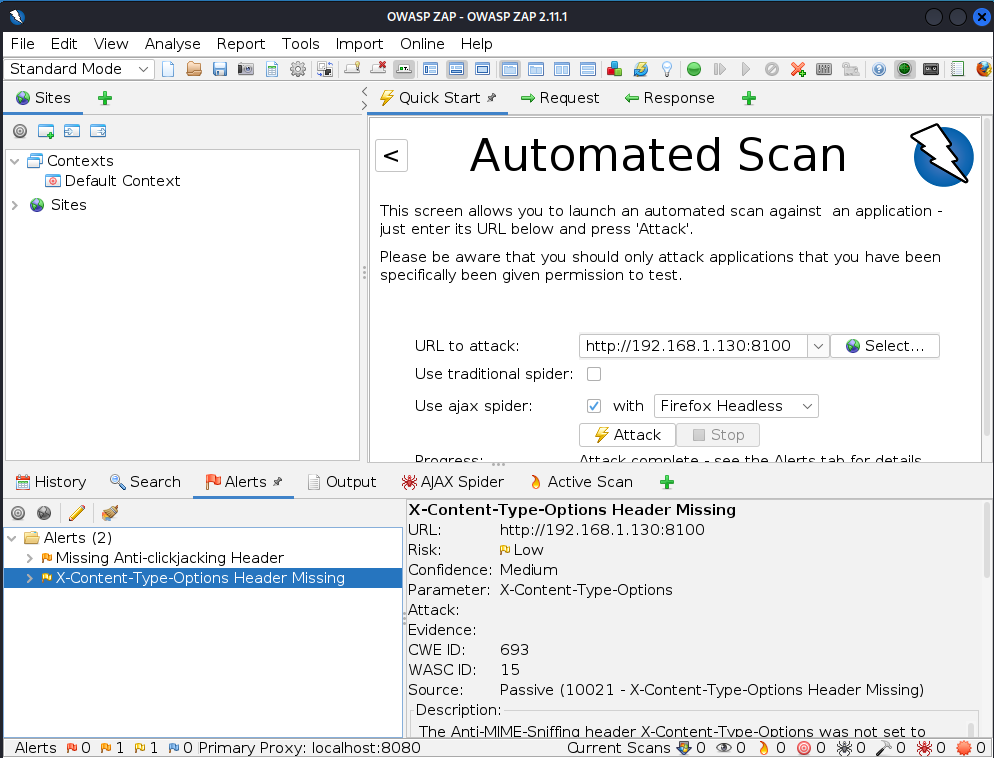
OWASP ZAP is a dynamic analysis scanner that might be used for pentesting of Moodle. As the Moodle is a widely known product, that has a visibility of the community, you unlikely will find a zero-day vulnerability. But as the OWASP ZAP have many different security checks, it can be used to check for various issues, such as sensitive information disclosure.
You can easily start the OWASP ZAP, enter the URL for attacking, and run the ZAP scan. Soon after that, you should get the results.
Final Words
Just like with any other software, Moodle has to be actively taken care of. Periodical updates is a must, as it will prevent the attackers from exploiting publicly known weaknesses (although you won’t protect from the zero-days).
This article gave you an understanding of the Moodle penetration testing, so, if you do use Moodle in your company, or you are a bug bounty hunter, now you are able to take the actions explained in the Moodle penetration testing checklist, to assess your software security posture.
Good luck hunting for the vulnerabilities!

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

