Cyber attacks nowadays are one of the biggest threats to many organizations and online businesses. If you are a blog owner, you surely do not want your website to be hacked. After all this is your baby that you put enormous effort into, created high quality content and expect long term returns for it.
If it does happen that you use WordPress, you might already know that historically it had many security weaknesses. Some of them might even lead to total takeover of the website. That’s why not only you should keep it up to date, but also take care of additional security precautions. For this purpose, we will discuss should you disable XML-RPC in WordPress.
Table of Contents
What Is the WordPress XML-RPC?
Before discussing the dilemma should you disable the XML-RPC, we will briefly explain what is the XML-RPC in WordPress.
When it comes to the XML-RPC in WordPress, it was created to define a standard for communication between WordPress and other systems.
Some key facts about the protocol that WordPress implements:
- XML-RPC is a protocol that was created in 1998
- RPC is an abbreviation for remote procedure calls
- The protocol uses XML format for describing the data
- HTTP protocol is used for transporting the data
By using this functionality, you were able integrate CMS with other applications. This means you can create, update, delete posts, get or edit comments, upload files, without using the WP directly.
This provides ability to integrate many of the WordPress functions in the third-party systems. Here you can find a full list of supported functions.
Core functionality of it is located in the root directory of WordPress, in a file called xmlrpc.php.
While for most of the cases the XML-RPC functionality is not needed, there is one reason to have it enabled.
Pingbacks and trackbacks are using the xmlrpc.php.
Both of them are used for notifying other websites about content you publish.
Trackback is used to send a notification to external blog when you link to it. Owner of the website, knows you are linking to it as your ping would end up in the comments of article you are linking to. You might potentially grab the owner’s attention and get a no-follow backlink.
Pingback is almost the same as trackback, however pingbacks are being sent automatically.
By disabling the WordPress XML-RPC you won’t be able to send and receive pingbacks and trackbacks. However, in reality both of them increase possibility of spam, so this might be a good change to make for your website.
Even though historically the XML-RPC was used as the main protocol for communicating with other systems, nowadays WordPress REST API has taken its place.
So, you should disable the XML-RPC, as it only creates additional security risk.
If you have no legacy systems or plugins, it is very unlikely that you still use the XML-RPC. But if so, you might have other security issues as you might use outdated components.
As an alternative, you should use the WordPress REST API.
You Are Constantly Getting XML-RPC Brute Force Attempts
If you are a WordPress owner, you can be sure that you experience this attack often. To illustrate this, I checked the logs of this blog itself (bughacking.com). Below you can see incorrect login tries for XML-RPC authentication.
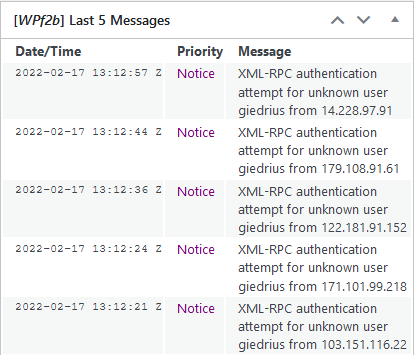
All of them happened few minutes before I checked the logs of my blog, so you can imagine how many of them are performed in 24 hours. Unfortunately, free version of the WP Fail2Ban plugin does not allow you to view more than last 5 event messages.
Plugins, such as WP fail2ban protects you from these attacks. Such plugins block the attacker from sending hundreds or thousands of malicious requests as soon as his activity starts looking suspicious.
Not only there is a problem of an attacker potentially guessing your password, but these requests also generate a significant traffic. If you are using a solid VPS for your website, this might be less of a problem. But if you are hosting on a server with less resources, this might become a headache.
If one or two incorrect authentication attempts to XML-RPC will not be flagged by the fail2ban plugin, request flooding will turn on the protective measures.
WordPress XML-RPC Can Be Used for DDoS Attacks
DDoS attack temporary paralyzes a system. During the attack multiple sources are sending high number of requests. Aim of the attack is to achieve such state of the system when it is not able to handle any new requests. In this case, legit user will not be able to use the website. Or the website would respond very slowly.
XML-RPC functionality can be used for DDoS attacks.
The pingback functionality in WordPress 3.5.1 and older version, is vulnerable. The attacker could send a specially crafted RPC request to your website. Such request would have an external host in the body. Vulnerable host then would execute the request by making a request to another website.
How to Disable XML-RPC?
Disabling the WordPress XML-RPC has some disadvantages. You should consider if there is any risk for your blog before making any changes.
Plugins, such as Jetpack will not have remote access to your website.
Also, if you are using some custom legacy applications, it might still be using this functionality.
Method #1 Creating New Rule in .htaccess File
Locate .htaccess file, which is usually in the root WordPress folder, and append the following rules:
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
This will deny external entities from accessing the file.
Method #2 – Delete the xmlrpc.php File
While this is one of the ways how you can protect your website from XMLRPC exploitation, this is not the best method.
It is only a temporary solution, as the WordPress will recreate this file each time you update WordPress. And keeping it not updated would introduce only more issues.
Method #3 – Another Way to Make Changes to the .htaccess Configuration
Adding a few lines to your Apache (or any other webserver) configuration will not take much time. The following additions to the .htaccess will restrict access to the file:
RedirectMatch 403 xmlrpc.php
ErrorDocument 403 forbiddenThe changes should take immediately. To check if it had taken effect, visit the xmlrpc.php page:

One of the biggest advantages over other methods of disabling the WP XMLRPC, is that server resources will not be exhausted. The attacker will get 403 Forbidden HTTP status code, and your server would not even process the request.
Note: If you are using LiteSpeed web server you might find the mentioned .htaccess rules not effective for it. But apparently, they work perfectly for Apache. For blocking XMLRPC in OpenLiteSpeed this rule works perfectly:
RewriteRule ^(/xmlrpc\.php|wp-trackback\.php) - [F,L,NC]Enter it in the Virtual Host -> Rewrite -> Rewrite Rules section. After graceful restart it should take the effect.
Method #4 – Use a Plugin
This is probably the easiest and least technical method of all the mentioned ones. You can download and activate the plugin Disable XMLR-RPC-API. It will take effect immediately, and the xmlrpc.php file will not be accessible for anyone.
You might find other plugins doing the same job. There are even more popular and with more downloads. However, make sure if they really do take effect.
I’ve tested a few plugins while writing this blog post, and the following plugin had not worked for me. From the plugin comments page, it seems that it does not work for everyone who uses newest WordPress versions.
How to Check if It Is Enabled on Your Website?
It is easy to check if you do have the RPC functionality enabled. A simple POST request with XML format data in the body will do the work:
curl -X POST -d ‘<?xml version="1.0" encoding="utf-8"?> <methodCall> <methodName>demo.sayHello</methodName> <params> <param> <value>admin</value> </param> </params> </methodCall>’ https://example.com/xmlrpc.phpServer responds with the following response when the XMLRPC is enabled:

Otherwise, you would get the “Access to this resource on the server is denied!” message.
You can also directly visit your website – https://example.com/xmlrpc.php. If the access is denied, you can be sure that it is restricted for everyone.
Final Words
It is important to keep your WordPress up to date. Outdated WordPress instance risks being hacked. This is also applicable to the plugins. The more plugins you have, the bigger is the attack surface. And of course, even if you keep the WordPress and the plugins you use up to date, there are different ways how you can increase the security.
One of the ways was explained in this article – by disabling the WordPress XML-RPC. In this way your installation will receive less malicious requests. As a result, the server will be less loaded (it will work faster for the users), and you will be sure that the attackers won’t exploit new 0-day XMLRPC vulnerabilities.
Stay safe!

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

