Sublist3r is one of the most widely used tools for enumerating subdomains. A Python based script that uses OSINT, can help you to identify every subdomain of the target. At the moment of publishing this article, Sublist3r has almost 6000 stars on GitHub. This shows that the tool is pretty popular and is one of the leaders in its category.

In fact, Sublist3r is even covered on the official CEH v11 study guide.
Sublist3r uses different methods for resolving the subdomains – it uses search engines such as Baidu, Yahoo, Google, Bing, Ask, it also uses various services, as Netcraft, DNSdumpster, Virustotal, SSL Certificates, Passive DNS, and finally it uses good old brute-force method.
This tool comes especially handy if you are a bug bounty hunter. In some of the cases, the organization that owns the bug bounty program allows testing … everything. But the natural question is what is everything? Before starting to search for bugs, you must understand the scope. And if the scope is defined like this:
*.example.comTool, such as Sublist3r, will help to identify each of the subdomains. By seeing the full picture, you will be able to prioritize the most important ones. This will help you to understand where you should put your effort into.
How to install Sublist3r on Linux?
The Sublist3r is on Kali Linux by default, but if you are willing to use the tool on any other Linux distribution, it is pretty easy to get it. It is on the PyPi repository. If you do not have the pip installed, you can do so with:
sudo apt install python3-pipAfter this, Sublist3r on Debian or other Linux distro, can be easily installed with the following command:
pip install sublist3rThis should not only install the tool itself, but also the needed dependencies. After the installation, you will get a warning:
WARNING: The script sublist3r is installed in ‘/home/YOUR-SYSTEMS-NAME/.local/bin’ which is not on PATH. Consider adding this directory to PATH or, if you prefer to suppress this warning, use –no-warn-script-location.
As the warning explains, /home/user/.local/bin directory is not in the path. You can see it for yourself by executing echo $PATH command.
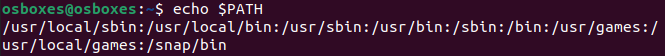
Great news is that you can fix it easily with this command:
export PATH="$HOME/.local/bin:$PATH"Needed directory will be added to the path, and you will be able to start the Sublist3r by simply calling its name:

Next section will cover the most common parameters of the tool.
How to use Sublist3r
Let’s check how we can use the Sublist3r on a real target. Tool has a few options:
- -h shows help.
- -b enables bruteforce module. Depending on the target you have permission to test on, brute force might not be allowed.
- -p with this parameter you might specify what open ports you want to search for. Only subdomains that have your specified ports open, will be provided in the results.
- -v provides results in a realtime.
- -t specifies the number of threads that should be used for the bruteforce.
- -e specifies search engines. By default, the tool uses everything, but you can specifically tell which ones should be used. Ex. sublist3r -e google,yahoo,virustotal -d example.com.
- -o saves results into a file.
- -n output without color.
You can simply start the tool with a command sublist3r -d example.com. Keep in mind that no brute force will be used.

Also, you might notice that there is an error – Error: Virustotal probably now is blocking our requests. This is a known problem that project maintainers should fix.
One thing to consider if you are trying to get the subdomains of a big target, is that not everything will fit into the terminal window. If you have a target such big as Google, that has near thousand of subdomains, you should write the tool output to a file. Not only you will be able to see all the results, but you will have this information for the future. You will be able to investigate it later, also compare if there are any new subdomains.
You can write the Sublist3r output to a file with additional parameter -o.
sublist3r -o subd.txt -d example.com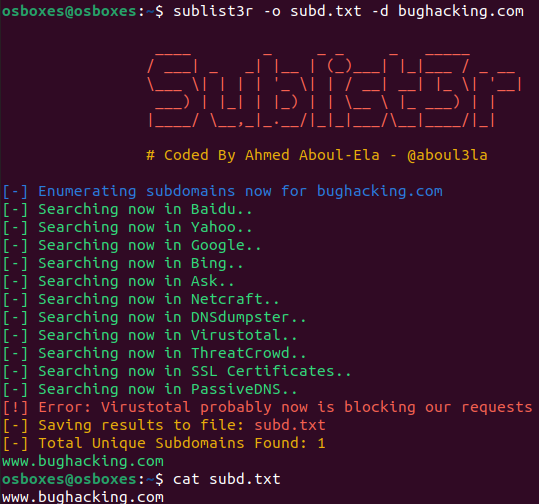
If you are willing to use the bruteforce module, you can do so with already mentioned -b parameter:
sublist3r -v -b -d example.comKeep in mind that for this example a -v parameter was added. Without using it, you would just have to wait for the bruteforce to finish in the darkness. Additional v parameter shows results in a real time, it means that every time a new subdomain will be resolved by the bruteforce, it will be shown interactively in the terminal.
Another cool feature of the Sublist3r, is that you can use it as a module for you Python script:
import sublist3r subdomains = sublist3r.main(domain, no_threads, savefile, ports, silent, verbose, enable_bruteforce, engines)
Conclusion
Subdomain enumeration is definitely one of the most important reconnaissance methods. Every hunting on a bug bounty program should include usage of a tool for subdomain enumeration, in order to understand the scope.
Keep in mind, that you can perform the subdomain enumeration only with a permission of the target’s owner.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.


Is this a app that I can install and use on my phone or not how much will it cost me
Thank you so much for this, it really helped me, cos I have been finding it difficult installing sublist3r