This is one of the most interesting beginner-friendly level rooms on Try Hack Me. If you are familiar with the Rick and Morty, well, this room is based on them – you have to help Morty find the 3 ingredients that will help Rick make a potion that will transform him from the pickle back to human. Without the long introductions, let’s start with the Tryhackme Pickle Rick room walkthrough.
Just like with any other THM machine, click on Start Machine, and let’s begin.
TryHackMe Pickle Rick Room Overview
The concept of this room is simple – you get a website, and you have to find three ingredients (and by knowing the Tryhackme concept, we can be sure that we have to find three flags located somewhere on the victim’s machine).
There are no clues on this, but it makes it even more interesting. In this way, you can try everything by yourself and you can test yourself if you know the pentesting basics good enough to work on your own.
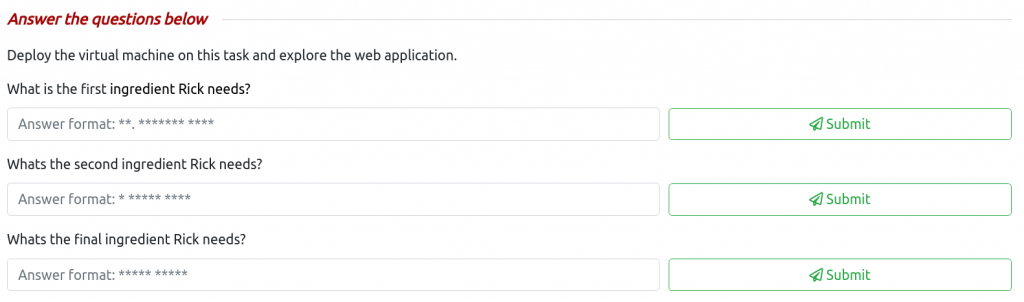
There are also no hints on the results submission page. Although we have some hints on the format of the ingredients:
- AA.AAAAAAA AAAA
- A AAAAA AAAA
- AAAAA AAAAA
This is not very helpful, although it hints us the number of letters in the words of the secret ingredients. At least we will be able to identify the ingredient when it will be in front of us.
Walkthrough
The first thing we should do after we’ve deployed the room is to enumerate hard. And what I mean by saying hard, is that you should try every effective method you know. And the key is to use effective methods, using two similar tools will not benefit you much.
Let’s start by running a nmap scan:
nmap -sC -sV IP_ADDRESSWhile other options might be as effective as these ones, -sC and -sV checks for the service versions and uses the default scripts of the open ports.
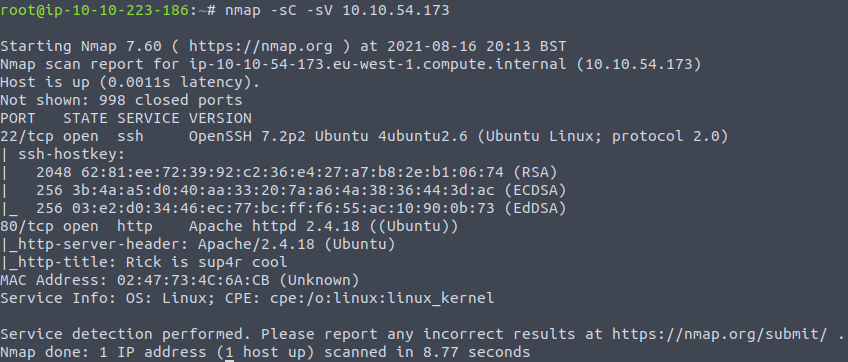
After the scan finishes. we can see that ports 22 and 80 are open. As we know that webserver is on port 80, we can run a web server scanner to check if there are any vulnerabilities that might be exploited by us. We can use Nikto for this purpose – web server scanner that comes by default with Kali Linux. A simple command will start the web scan:
nikto -host IP_ADDRESS
Great, after the scan is executed we can see a few things. First of all, it shows used version of the server, which is Apache 2.4.18. Even though it might benefit us, there is another thing that is more interesting for us.
Nikto says that the Robots.txt file does not contain “disallow” entries and does not follow the usual format. Let’s keep this in mind as it will help us with the Tryhackme Pickle Rick walkthrough.
Let’s continue with the enumeration. What we will do next, we will try the directory brute force. Even though we can use tools such as Dirbuster to perform directory brute force, this time we will try GoBuster. Let’s use one of the Dirbuster wordlists. If you are using the THM attack box you can find the wordlist by the following path /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt. Start the GoBuster from the command line:
gobuster dir -u 10.10.186.87 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,phpWhat is worth mentioning is that this command has -x option, after which we set the extensions. GoBuster will use the passed extensions during brute force. So, if the word “login” is in the wordlist, the tool not only tries to use “login”, but also “login.html’, and ‘login.php’. And as you will see after a moment this is very helpful in our case.

After the attack is finished we can see that a few pages were found. It is a great idea to check all of the pages to find any useful information.
As our nmap scan shows the webserver is on port 80, you can visit the home page with your browser.
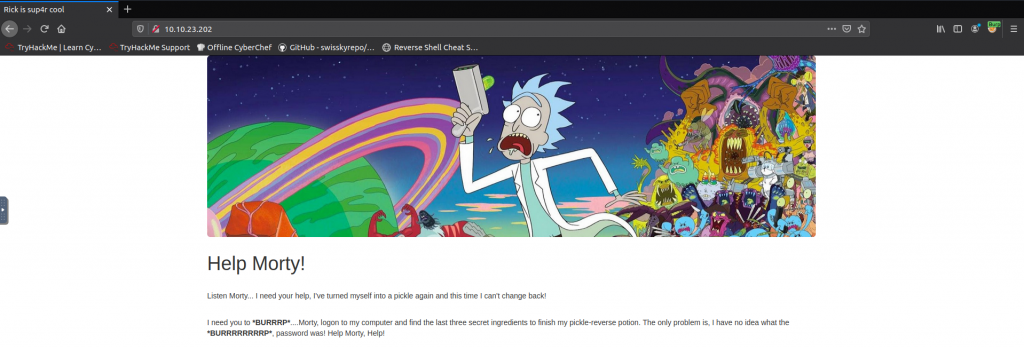
From the first glance, there is nothing on the website, only one page. That’s weird. But we have to be quick and help Rick. If you have been stuck on this very first task of the room do not worry, this is why this TryHackme Pickle Rick walkthrough was made for.
The first thing we can check, is the source code of the page, and bingo! There’s a username.

But where do we use it? As there is an SSH port open, we might try logging in with the given username. This is definitely a legit guess that might work. I encourage you to do so in this room just for learning purposes – ssh R1ckRul3s@VICTIM_IP. Sadly, this does not work. And we have to look somewhere else.
During the directory brute force attack, we had found out that there is a page called login.php. Let’s try visiting it.
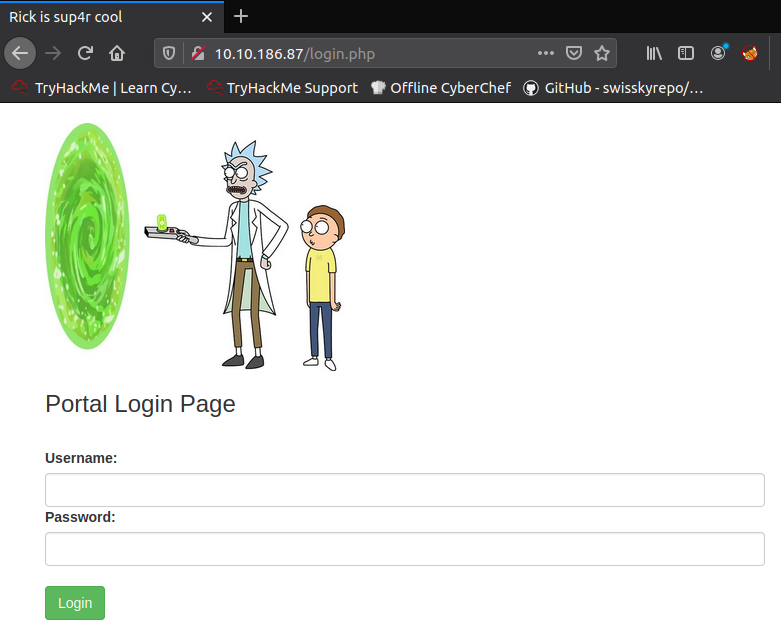
We can see that there is a login page. We know the username (R1ckRul3s), but how about the password? In order to find it we have to investigate our enumeration findings. Remember the robots.txt file that was found? Nikto alerted us that it looks weird. Let’s check it.

And we see that there is some kind of text. Let’s try it as a password on the login.php page.
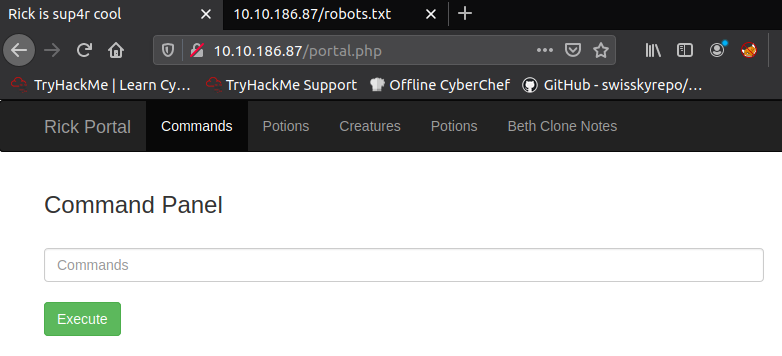
Great success! We had accessed the admin panel. We can execute the ls command and see that there are some files and one of them is a secret ingredient.
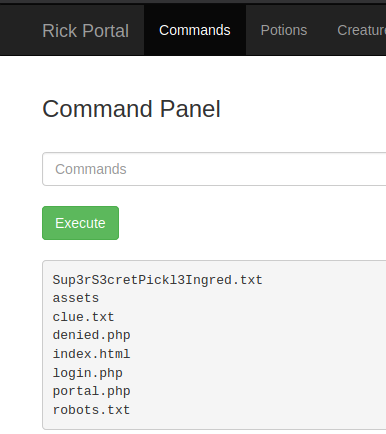
But can we use cat command to read it? Unfortunately, this is not that easy. Also, other pages from this panel are restricted.

However, after a little bit of trial and error, you might find out that another command, less, is not forbidden. By executing less Sup3rS3cretPickl3Ingred.txt we can successfully read the file content.
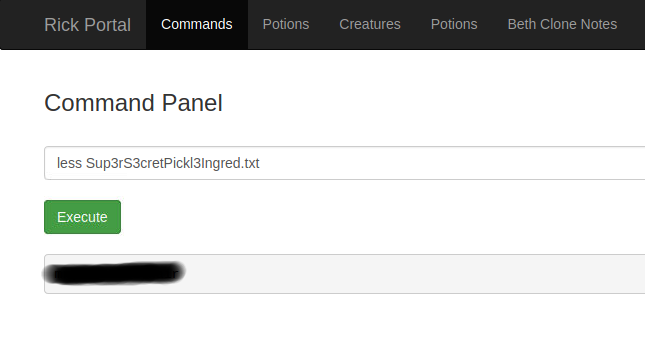
Perfect, now we have the first flag. But how about the other ones? If you paid attention, you might have noticed that there is a clue.txt file in the directory. Let’s use the same less command to read the contents of it.

And what does it mean, is that we have to keep digging. Even though you can try using the reverse shell, this is not necessary in our case. Our further investigation shows that we can run as sudo without a password.
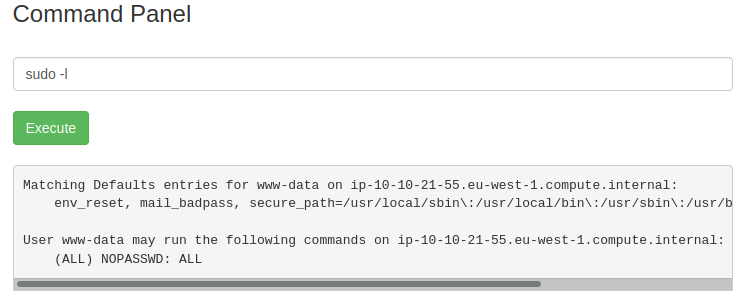
The possibility to use sudo is very handy for us, as without it, we would not be able to see any files outside our current directory. As we are familiar with the standard flag location, a great place to start searching for it would be the home directory of the user. By using the ls command we can find out that the user is rick. And if we’ve checked what’s inside his home directory, we can see that there is the second ingredient and our needed flag, which is called second ingredients.

Again, with the help of less command, we are able to retrieve the file contents – sudo less /home/rick/’second ingredients’.

After a further investigation with the sudo ls command, we can also see that there is a third flag in the /root directory.
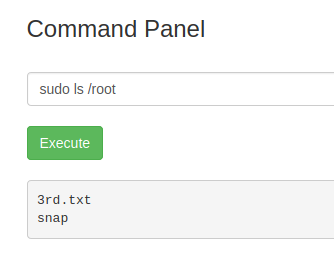
Aaaaand – success. We now have the third and last flag!
Final Words
If you liked this one, you might find another great room on the Try Hack Me. For example, if you had not already checked the Vulnversity room, it is a good one to continue. And if you are stuck, you can always use the walkthrough.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

