Subdomain takeover is one of the vulnerabilities that might really hurt for the company if exploited. If you want to identify it, specialized tools and methodologies have to be used. This is the type of vulnerability that requires technical knowledge, experience, and a little bit of luck to find. Today we are going to cover the best subdomain takeover tools for bug bounty hunting.
If you are bug bounty hunter, you will probably want to aim at to find the subdomain takeover vulnerability. Not only this is easy hanging fruit that gives you a satisfaction of finding a bug, but the companies often pays well for them.
As an example how rewarding it is to find a subdomain takeover vulnerability, you might take a loot at the bug bounty reports. Cristian Cornea had made a review of the top subdomain takeover bug bounty reports. The case study shows even the big companies, such as Starbucks, Uber, Snapchat, Twitter, and others, can be affected. And these companies tend to reward well for this vulnerability – the biggest payout for the subdomain takeover was 8 000 dollars.
Table of Contents
What is the Subdomain Takeover?
To start with, we must talk what is the subdomain takeover vulnerability. And most importantly, what potential consequences it might cause for the affected company.
Subdomain takeover might occur when the subdomain, that is used by the company for one or another reason, is taken by external party. This might happen if the CNAME in the DNS is not registered (yet). Or maybe it was removed.
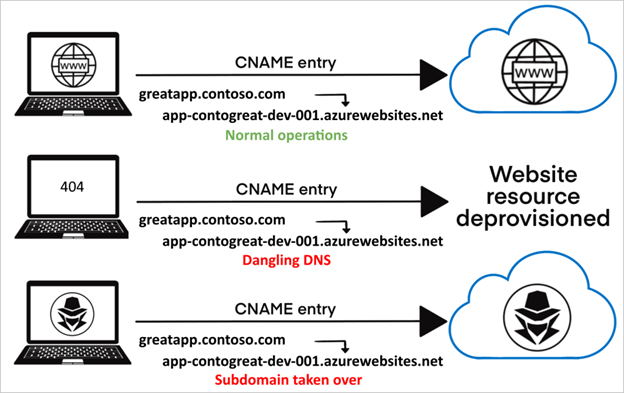
To illustrate the vulnerability exploitation, we might consider this situation:
- Company hosts third party application on one or another subdomain (in this example, it is app-contogreat-dev-001.azurewebsites.net)
- This application is referenced from the main application, ex. greatapp.contoso.com is pointint to the one hosted on Azure.
- Subdomain app-contogreat-dev-001.azurewebsites.net is not being used anymore – it might be deleted by mistake, or for any other reason.
- The attacker registers the same subdomain and has full control of it.
- Subdomain is used by the attacker for phishing or any other purposes. As it is still referenced by the main application, there is a risk that end users, without being aware about it, might become victims.
As you might see, if there is a dangling DNS record for the subdomain, it might be registered by the attacker. During the active development, a subdomain might be implemented in the application, that accessible publicly, even before the subdomain is registered. If the company is big enough, or it is under the radar of the bad guys, this can be exploited in a matter of time.
Most of the big companies have many domains and subdomains in use. While a small company, might have just a few, companies, such as Google, has thousands of them. It might become burden to identify all of the subdomains, so there is a chance that a big company is vulnerable to the subdomain takeover. That‘s why the vulnerability should not be overlooked and best subdomain takeover tools must be used to found it.
Best Subdomain Takeover Tools
I’ve made a list of the best subdomain takeover tools. While most of them do the same job, they differ in features Both, beginners and those looking for specific features will find useful tools in this list.
Subjack
Subjack is a subdomain takeover tool written in Go. It can be used for concurrent scanning of subdomains (this is why it’s written in Go – Golang is good for concurrency). While some of the other alternative tools do support concurrent scanning, this one was built specifically for that.
While one of the strong sides of the tool is performance, it has more great features:
- Custom fingerprints, that allows you to add more services
- Enforces SSL usage. This might return different results that might potentially be overlooked by other tools
- Can be integrated into your workflow. If you are a developer, this would provide you confidence that you are not leaving dangling subdomains
Tool can be installed with Go. To check if you have Go on your system, execute command ‘go” in the terminal. If you get the help menu, you are good to go. If not, you must install it. I have the Golang installation instructions in my other article.
Anyway, back to the installation:
go get github.com/haccer/subjackAfter this, you can check the help menu by simply calling the tool:
subjack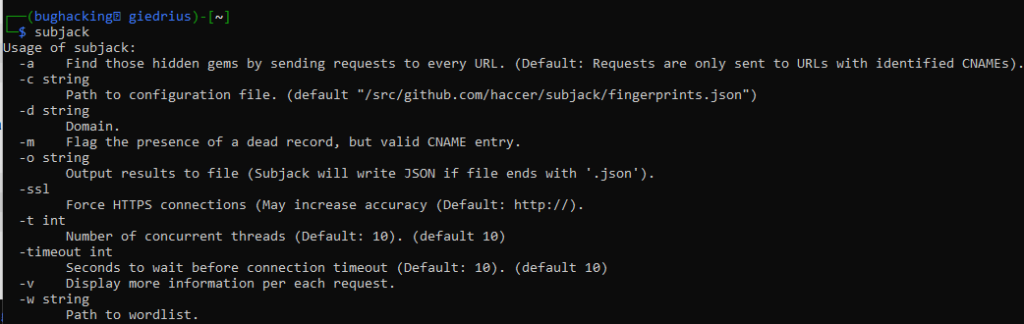
If you want to scan a number of subdomains at the same time, this command would do the trick:
subjack -w subdomains.txt -t 100 -timeout 30 -o results.txt -sslSub404 – Tool for Checking Subdomain Takeover
Another tool to check subdomain takeover while bug bounty hunting, is the Sub404. This tool is written in Python, but it implements asynchronous scanning, so it is fast. Tool lets you to automate task of searching for potentially vulnerable subdomains in scale.
To install the Sub404 you must have Python 3.7 or newer.
git clone https://github.com/r3curs1v3-pr0xy/sub404.gitAfter cloning the repository, install the needed dependencies:
cd sub404 && pip install -r requirements.txtSub404 also implements two additional tools, that provides you extra value – Subfinder, and Sublist3r. However, both of them are optional, and should be installed manually. If do not want to use them, the installation is done. You can test if installation went fluently:
python3 sub404.py -hThis is the result you would expect:
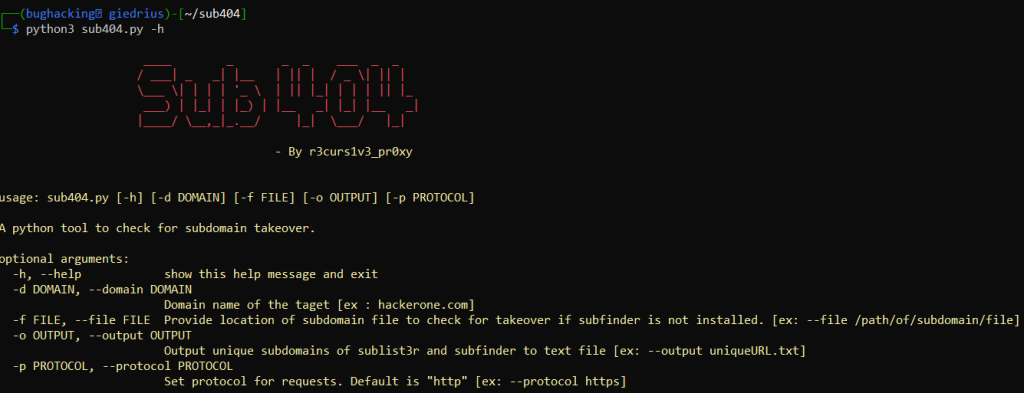
Alternatively, you might run it as a Docker container:
docker build -t sub404 .
docker run --rm sub404 -hIf you do have the Sublist3r installed on your system, you can use the following command:
python3 sub404.py -d example.comBefore checking for the takeover vulnerability, it will perform subdomains identification. But if you do not have the additional tool, you must provide subdomains by yourself in a file:
python3 sub404.py -f subdomains.txtSome more useful options:
| Flag | Description | Example |
|---|---|---|
| -d | Domain name of the taget. | python3 sub404.py -d noobarmy.tech |
| -f | Provide location of subdomain file to check for takeover if subfinder is not installed. | python3 sub404.py -f subdomain.txt |
| -p | Set protocol for requests. Default is “http”. | python3 sub404.py -f subdomain.txt -p https or python3 sub404.py -d noobarmy.tech -p https |
| -o | Output unique subdomains of sublist3r and subfinder to text file. Default is “uniqueURL.txt” | python3 sub404.py -d noobarmy.tech -o output.txt |
| -h | show this help message and exit | python3 sub404.py -h |
Tko-subs
Tko-subs is a tool written with Golang, that helps to identify dangling subdomains. It helps to search for pointings to CMS providers, searches for links to non-existent hostnames, misstyped NS records.
What’s great about the Tko-subs tool, is that you can specify your own CMS providers. All you have to do is to do the providers-data.csv file and insert CMS name, CNAME value, and string that is used to identify the vulnerability. This makes the tool customizable.
Back to the Tko-subs installation. It can be downloaded with the Go:
go get github.com/anshumanbh/tko-subsAfter that, you can check the help menu with tko-subs -h:
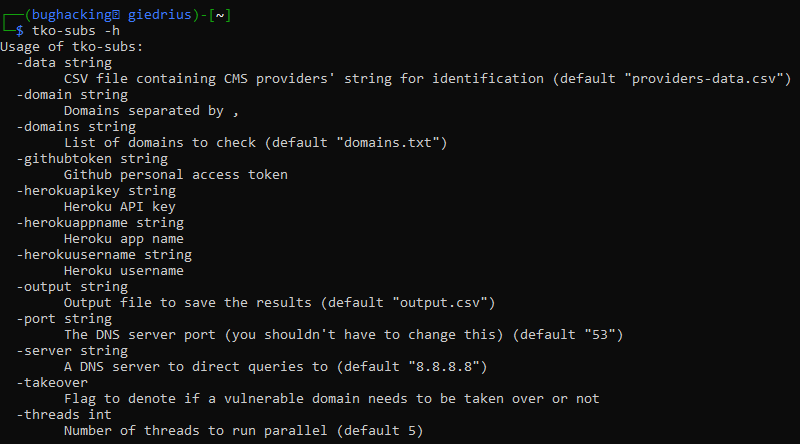
If you want to execute the takeover with the tool, you will need to provide additional information. Such as GitHub personal access token, or Heroku username and API key. But if you do not want to do it, and you only need to identify subdomains that might be potentially taken over, you can use this tool without additional parameters.
Additionally, you will need to install some Go packages:
go get github.com/bgentry/heroku-go
go get github.com/gocarina/gocsv
go get github.com/google/go-github/github
go get github.com/olekukonko/tablewriter
go get golang.org/x/net/publicsuffix
go get golang.org/x/oauth2
go get github.com/miekg/dnsTo run the tool you can execute the following:
tko-subs -domains=domains.txt -data=providers-data.csv -output=output.csvBy default the providers-data.csv file has 45 (at the moment) services. But you can always add more. The file is provided in the GitHub repository.
Takeover
Takeover is a subdomain takeover tool lets you to check if the targets points to one of the subdomains that does not exist anymore (the subdomain might have been deleted, or simply removed). Tool checks for the subdomains of most common services.
Process of installing Takeover is pretty straightforward. All you need to do, is to download the code from GitHub repository, and run the downloaded Python script:
wget -q https://raw.githubusercontent.com/m4ll0k/takeover/master/takeover.py && python3 takeover.pyTool has different options:
-d Set domain URL (e.g: www.test.com)
-t Set threads, default 1
-l Scan multiple targets in a text file
-p Use a proxy to connect the target URL
-o Use this settings for save a file, args=json or text
-T Set a request timeout,default value is 20 seconds
-k Process 200 http code, cause more false positive
-u Set custom user agent (e.g: takeover-bot)
-v Verbose, print more info
As an example, if you want to scan a specific domain and want the tool to provide verbose results, the following command would do the trick:
python3 takeover.py -d www.example.com -vCan I Takeover XYZ?

Can I takeover XYZ is a GitHub repository that has a list of services that frequently becomes the targets of the subdomain takeover exploitation.
What is worth explaining that there is nothing wrong with those services. It’s just that these are popular services that are implemented in a significant number of systems. And if the system is vulnerable to subdomain takeover, there is a high chance that the taken over subdomain is one of those listed in Can I takeover XYZ? list.
The GitHub repo helps you to find the dangling DNS records. Right now the list has over 60 services. Fingerprint of most of them is provided. The fingerprint might help you to identify if there is any subdomain on a given system, that might potentially by taken. Repository is constantly being updated and has the attention of the cyber community.
This is not that type of tool where you paste a command into the terminal and wait for the results. But without a doubt, this is a great reference to look at while you are searching for vulnerabilities and are employing other subdomain takeover tools.
How to Protect from Subdomain Takeover Attacks?
While some of the cloud providers do have counter measures that prevents subdomain takeover from occurring, other do not have such protections. There are various cases when the vulnerability could be present.
Finding the subdomain takeover with dedicated tools is just half the job. If you are writing a report, and expect a payout for your effort, you must fully understand the attack. High quality report increases the success rate. And on the other hand a poorly written report, even if a high severity vulnerability is found, might be rejected.
If you want to have the full picture of the vulnerability you found, you must understand how to protect from such attacks. In this way you will be able to explain the potential impact of the vulnerability and remediation techniques.
- Regulary audit DNS records. Make sure you identify if there are any dangling subdomains. The subdomain that is used, might become forgotten, especially if the person, that created it, does not work on the project anymore. Periodically audit the DNS configuration, especially if there are frequent changes.
- Choose reliable vendors. Some of the vendors protect their users from subdomain takeover. Others, less reliable, does not take these extra precautions. Make research and find out if your vendor takes the precautions.
- Use monitoring tools to identify all your subdomains. The subdomains used by your application might be identified during a penetration test. But a better approach is to use some kind of third party tools that monitors the external attack surface.
Final Words
Subdomain takeover is a vulnerability that should not be overlooked. All companies must take it seriously, as this might lead to website defacement, phishing, stealing of cookies, CSRF attacks, and other attacks. If you are a bug bounty hunter, this is the vulnerability you might want to spend some time searching for it. It pays well, and you are creating great value for the company and preventing potential attacks.
I hope you will find value in the list of the best subdomain takeover tools.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

